Principal, Xamax Consultancy Pty Ltd, Canberra
Visiting Professor, Baker & McKenzie Cyberspace Law & Policy Centre, University of N.S.W.
Visiting Professor, E-Commerce Programme, University of Hong Kong
Visiting Fellow, Department of Computer Science, Australian National University
Prepared for submission to the IFIP Int'l Conf. on Decision Support Systems (DSS2004), Florence (Prato), 1-3 July 2004
Version of 9 December 2003
© Xamax Consultancy Pty Ltd, 2003
This document is at http://www.anu.edu.au/people/Roger.Clarke/EC/ICDec.html
The disappointing adoption rates of Internet commerce by consumers are examined by contrasting two alternative sets of assumptions about the critical stimulants and impediments. It is suggested that the focus needs to be switched from merchants' needs to consumers' needs, and that the 'consumers as quarry' mind-set needs to be abandoned in favour of approaches more attuned to the distinctly different world of the Internet, cyberculture and cyberspace economics.
Internet commerce is a useful term to describe the placing of orders and the effecting of payment using a web-site. The particular combination of technologies used during the first decade has been HTML including the forms feature, web-browsers and web-servers communicating via HTTP including the GET and POST methods, CGI-scripts, and gateways into the EFT/POS System (Clarke 2002b). A popular interpretation of the commencement data for Internet commerce is October 1994, when the hotwired site was launched. The scope of this paper is limited to consumer Internet commerce, sometimes referred as 'B2C'. It does not address B2B or government procurement.
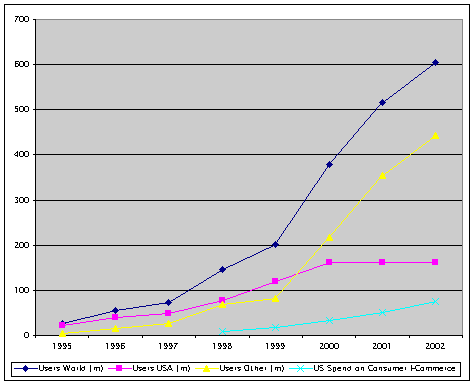
Growth rates for the primary Internet usage metrics between 1994 and 2003 have been enormous. But the growth rates for Internet commerce have been much lower. For example, Exhibit 1 provides estimates of year-on-year growth, between 1995 and 2002, in the number of Internet users worldwide, in the most mature region, and in the rest of the world, juxtaposed against one estimate of the growth-rate of consumer spending in the most advanced market. (The user -counts are from Benschop 2003, and the consumer spend estimates from NUA 2003, attributed to Forrester Research. See also Pew 2003).
1995 1996 1997 1998 1999 2000 2001 2002
Users World (m) 26 55 74 147 201 378 516 605
Increase % p.a. - 112% 35% 99% 37% 88% 37% 17%
Users USA (m) 22 40 48 78 120 162 162 162
Increase % p.a. - 82% 20% 63% 54% 35% 0% 0%
Users Other (m) 4 15 26 69 81 216 354 443
Increase % p.a. - 275% 73% 165% 17% 167% 64% 25%
US Consumer 8 18 33 52 76
Spend $billion
Increase % p.a. - 125% 83% 37% 46%

The proportion of Internet users who participate in Internet commerce appears to be below 20% (e.g. TNSG 2002). Even in the nation that would appear to have reached the highest level of maturity, the U.S.A., only 32% of users are 'Online Shoppers', and the TNSG estimates suggest that the spend per user there is of the order of $1,500 p.a. In other leading countries, the proportion of Internet users who were reported as "having purchased online in the 6 months to September 2002" were Canada 34%, Sweden 26%, UK 23%, Japan 19% and Australia 18% (NOIE 2003).
Exhibit 2 provides an indication of the enormous diversity in the extent to which access to the Internet is available (The user-counts are from NUA 2002, and the populations from PRB 2003). This does not take account of high-intra-regional diversity; for example, Asia/Pacific includes many late-adopter countrie, but also the high-penetration nations of Korea, Japan, Australia, Singapore and Hong Kong.
Users Population Penetration
(million) (million)
Africa 6.31 840 1%
Asia/Pacific 187.24 3668 5%
Europe 190.91 728 26%
Middle East 5.12 130 4%
Canada & USA 182.67 319 57%
Latin 33.35 531 6%
America
World Total 605.60 6216 10%
There are many possible explanations for the low uptake. One is
that the proportion of Web users who are interested in social activities to the
exclusion of economic ones remains large (in which case it might stay like
that). Another is that there is a long lag between the time people become
Internet users and the time they become Online Shoppers; but if so then that
lag would seem to be as long as 4-5 years.
This paper is a further contribution in a series of analyses that has investigated the conventional design of Internet commerce sites. The proposition developed in this paper is that there is a poor fit between that design and consumers' needs. The particular focus here is on the decision models that are assumed for both consumers and merchants.
The paper commences by proposing a simple model of the decision made by a trader. An assessment is then undertaken of the conventional way in which that model is applied. An alternative application of the model is then proposed, which builds on an appreciation of the differences between broadcast-era consumer marketing and the Internet age. Evidence is provided of the ease with which the alternative approach can be implemented.
In order to distinguish between alternative views of Internet commerce, it is necessary to use an abstract general model of the decision made by a participant in a commercial transaction. The following is proposed:
A trader performs a trade if they perceive strong enough motivators to perform the act that effects the exchange, and insufficient demotivators to dissuade them from performing that act.
Some motivators and demotivators relate to the tradable item, e.g. measures of its quality. Others relate to the transaction, e.g. the price, the timing of its execution, and the risk-allocation in the event of contingencies such as loss or destruction of physical goods en route to delivery.
The following sections distinguish two alternative views on the basis of the different factors that are assumed to constitute the important motivators and demotivators.
This section presents an interpretation of the conventional views adopted by Internet merchants since the launch of Internet commerce in late 1994. This is then used as a basis for identifying assumptions about motivators and demotivators, and for the assumptions about what trust is.
The early movers within the business community perceived the Web as a new medium for advertising, with the additional attraction of enabling interaction with the consumer. For example, Schrage (1994) heralded the arrival of business in cyberspace, trumpeting that "the economics of advertising, promotion and sponsorship ... will shape the virtual realities we may soon inhabit ... Cyberspace's commercial future is inevitable. There will be billboards along the Information Superhighway". Conventional business models were to be applied to the net. On-line services were to enable marketers to achieve 'one-to-one relationships' with individual consumers (Peppers & Rogers 1993).
Within 2 years, the sad reality had crept up on the 'web as billboard' notion: "Unless content providers can do something brilliant immediately to boost the ad community's per capita investment in this medium, they will bleed additional millions over the next four years" (Madsen 1996. See also Bayers 1996 and Voight 1996).
In the early 1990s, a number of proprietary on-line services had been on offer. The Source, Prodigy, CompuServe, GEnie and Apple eWorld were unable to withstand the challenge that the Web presented (e.g. Wolfe 1994). As late as 1995, on the other hand, two major players sought to compete with the open public Internet, by developing closed communities. AOL had a strong position, and sustained a business based on new online users for a further 5-6 years. Microsoft Network (MSN), on the other hand, succeeded only in quickly disposing of a considerable amount of the super-profits from the company's few financially successful divisions (Nollinger 1995, Caruso 1996).
A further attempt was made to constrain the Web to the broadcast-media frame of reference. Push-technologies such as PointCast and Castanet were hailed as the future of Internet commerce (e.g. Kelly & Wolf 1997). Yet, within a mere 12 months, it had been discovered that "The most surprising roadblock for push ... comes not from technology, but from the intended audience. Push media's promises are often met with outright resentment from computer owners glad to be free of TV's broadcast model. ... Consumers are smarter than media organisations thought" (Boutin 1998).
In the third quarter of 1998, a new round of marketing fervour swept into vogue. The means whereby corporations would capture the hearts and minds of consumers was the 'portal'. A portal was meant to be the automatic first-port-of-call for large numbers of captive net-users eager to part with their money. They were therefore expected by this particular round of soothsayers to command high advertising-rates and click-through fees, plus commissions on resulting sales (Nee 1998, Thornberry 1998). Five years later, the notion continues to stagger along, undergoing periodic re-packaging and exciting re-launches.
A primary focus from the late 1990s onwards has been the surreptitious capture of personal data, with the intention of supporting mass micro-marketing. The first requirement was for data that identifies the individual. In some cases this might arise from willing interactions, or be otherwise consensually provided, as is the case with the 'click-trail' around a company's web-site. But less honest methods were widely used, such as pseudo-surveys and competitions. And surreptitious measures were harnessed, such as cookies, Javascript, Java applets and ActiveX controls. And new ones were devised, such as single-pixel gifs, also known as 'web-bugs'. Ignoring the lessons that could have been learnt from the demise of Lotus Marketplace (Winner 1991), Doubleclick breached customer expectations. But it was eventually forced to withdraw its profiling product (Olsen 2002). Acxiom continues to breach consumer rights by accumulating vast collections of data, and Direct Marketing Associations publish empty codes (e.g. DMA 2002), and negotiate with governments to avoid the imposition of consumer protection regulatory measures.
Despite the privacy impediment having been drawn to net-marketers' attention many times since 1995, they have still not assimilated the message, and researchers in the area are forced to continually to re-cycle it (e.g. Hoffman 2003).
A further area of threat to consumers' interests is now commonly referred to as 'identity management'. The first product to become well-known was Microsoft's Passport, which gained a vast, although highly volatile, user-base when it was implemented for the Hotmail service that the company had acquired. In schemes of this kind, a person identifies themselves to a widely-available service (e.g. by typing in a username), and provides additional evidence to enable authentication of the identity they are claiming (e.g. by typing in a password). That service can then provide assurances to other services that the person has provided the appropriate evidence.
The two main candidates, MS Passport and Liberty Alliance, together with AOL's longstanding Screen Name scheme and the banking sector's Identrus, all appear to be predicated on a single identity for each user. They are designed to benefit merchants, evidence very limited involvement of consumer interests, are concerned primarily with the acquisition of approval from consumers, and give very little attention to specific, informed and freely-given consent, or even security (EPIC 2000-).
At this stage of development of identity management schemes, pre-registration procedures include little or no authentication of the person's identity. On the other hand, the manner in which they are promoted, and the discussions rumoured to have been held between the promoters and national governments, suggest that this may change. As agencies seek ways of implementing eGovernment inexpensively, they are considering moving beyond mere outsourcing to enter into partnerships with the private sector. They may be prepared to trade their citizens' privacy as part of the bargain.
During 2002-2003, owners of digital or digitisable content have become increasingly frenetic in their attempts to protect their content against appropriation by non-payers, and thereby sustain their longstanding business models. Copyright laws have been significantly extended to further benefit copyright-owners, and technological tools are being developed and deployed in an attempt to rein in what large corporations perceive to be anti-social, and worse still anti-economic, behaviour (Clarke & Nees 1999, EPIC 2002-). By mid-2003, associations representing the large music-recording corporations were suing grandmothers and 12-year-old children (Wired News 2003).
Based on a decade of not very successful attempts at consumer marketing, some inferences can be drawn. Corporations, in their singleminded pursuit of shareholder value have adopted language that uses aggressive metaphors drawn from militarism, law enforcement and hunting . A promotional program is a 'campaign'. Future customers are initially perceived as 'targets', and a sub-set of them are identified as 'suspects'. Customers are 'acquired'. Eyeballs are 'captured'. The consumer is seen as 'quarry', in the two senses that consumers are 'game' whose role in life is to be hunted, and that consumer data is there to be mined (or 'quarried').
Applying the decision model outlined in section 2 above, the first aspect of significance is that conventional views focus on the decision by the merchant to sell to the consumer, and pay much less attention to the decision by the consumer to buy.
Under this approach, it appears that the motivators for merchants are not so much the margin on the sale as the inexpensive acquisition of a repeat-buyer, from whom a stream of sale-margins can be gained.
The demotivators for merchants are one-time buyers who don't return. To combat this, means are sought to achieve 'customer lock-in' (usually referred to using the euphemism 'loyalty'). In the absence of much prospect of raising customers' 'switching costs', the focus is on 'capturing their eyeballs' by encouraging them to remember the site, bookmark it, and make frequent visits. The probability of a one-time buyer becoming a repeat-buyer is assumed to be enhanced by gathering data about the person and their behaviour, which can be used to make offers that will be attractive to them.
The motivators for consumers are assumed to be embodied in the image that the merchant projects. This tends to involve colour and excitement, familiarity with the 'brand', and in some sense 'ease-of-use'. It has little to do with price, choice, or terms of trade.
The demotivators for consumers are seen as lack of the properties that the merchant's logo, colour-scheme and catch-phrases project, combined with superior motivators emanating from competitors.
During the decade of slow growth, it has become mainstream to attribute slow adoption to lack of consumer trust. Trust is perceived to be undermined by the lack of the `comfort factors' of physical places, such as body-signals, hand-shakes, and a physical footprint for the merchant. Initially, the discussion focussed on a lack of readiness by consumers to type credit-card details into web-forms. Data transmission security measures (in particular SSL/TLS) were prescribed, but they appear not to have overcome consumer reticence.
The focus shifted, and eTrust was asserted to depend on authenticated identities for all parties. For merchants, this was implemented by means of the SSL/TLS digital signature feature, but relying on all-but-valueless certificates.
For their part, consumers were always unlikely to be cajoled into parting with good money for something as mysterious as a 'private key' and a 'digital certificate' that would together enable their browser to affix a 'digital signature' to each message it sent. So consumer identity remained reliant on self-declared information, augmented by whatever could be extracted from credit-card details, physical delivery addresses, consumer credit bureaux, HTTP traffic including IP-addresses and cookies, and data matching.
An alternative approach can be adopted, using the same decision model, but with different parameters. Many of these insights are far from new. Many are readily detectable (even if only tentatively formulated, or over-hyped) in such early papers as Hoffman & Novak (1997), and Kelly (1997).
This section commences by outlining the rationale. It then suggests a set of motivators and demotivators, and an interpretation of trust, that are consistent with that philosophy.
The Internet is technically different from the predecessor media of billboard, broadcast radio and broadcast television. It is also very different from cable television services, because they are fundamentally asymmetrical (i.e. high bandwidth outwards to the consumer, low bandwidth back), whereas the Internet assumes relative symmetry.
Variants of broadcast can be delivered over the Internet; but the infrastructure is fundamentally permissive of 'pull' as well as 'push'. HTTP, over which consumer Internet commerce is built, is a fundamentally request-response protocol, i.e. 'pull'. This alone should have been enough to throw some doubt on the proposition that conventional consumer marketing principles developed in the broadcast era were applicable to Internet commerce. To that must be added the spam phenomenon, which exploits SMTP's 'push' capability. Spam has soured consumers' attitudes to marketers to an extent never seen before.
There are additional factors to consider, beyond the technology itself. When the Internet became available beyond research circles in 1992-94, the initial reaction was a wave of enthusiasm that dramatic change was occurring. Over time, there has been something of a reaction against that view. Law enforcement and national security agencies have made some inroads into traceability (e.g. Clarke et al. 1998, BBC 1998). And copyright owners have made some headway in their attempts to constrain and to track people who breach their copyright (e.g. Clarke 2001b).
But it would be wrong to suggest that the initial reaction was wrong. Many of the differences that the enthusiasts of the early 1990s extrapolated from do indeed exist, and are indeed leading to fundamental change in many aspects of societies, economies and politics. Two key aspects of that change are highly relevant.
Firstly, people's behaviour in cyberspace is different from that in the physical world. The values imbued by the pioneers have been attenuated by the arrival of many millions of 'late adopters', but a large proportion of the newcomers, as their experience matures, evidence adoption of those same values. A mature science of cyberculture has yet to emerge, although tentative analyses do exist (in particular Hiltz & Turoff 1993 and Rheingold 1994; but see also Hauben & Hauben 1997 and Kollock & Smith 1999). Exhibit 3 provides a checklist of the elements of 'cyberculture ethos'.
Internet merchants therefore need to appreciate cyberculture, and devise their offerings to work within that context, rather than trying to carry over conventional mass marketing notions.
A second key consideration is cyberspace economics. There have been many attempts to explain the differences from conventional market economics. A metaphorical approach was provided at the very dawn of Internet commerce by Rheingold (1994), which distinguishes 'barn-raising' from 'horse-trading'. Shortly afterwards, Ghosh (1998) referred to a 'cooking pot', which "keeps boiling because people keep putting in things as they themselves, and others, take things out". Meanwhile, Raymond (1998) offered an early explanation of the economics of open source.
The digital era gives rise to an abundance of content, which demands a very different form of economics compared with the neo-classical school of thought that was developed to explain markets in scarce real estate, goods and services. On top of that, the mutuality inherent in cyberculture demands an economics of exchange that is not based on direct and immediate reciprocity, but on indirect and/or deferred consideration, i.e. passing value earlier or later, and/or to someone other than the party from whom value is received.
Early writings were socialist in tone, suggesting a revolution in economic thought was needed. Subsequently, economists have drawn attention to the pre-existence of relevant bodies of thought, in particular in 'network economics' (e.g. Economides 1996), and 'information economics' (Lamberton 1971, 1996). For a business-oriented rendition that is far from heralding revolution, see Shapiro & Varian (1999).
To achieve the breakthrough and encourage consumers to adopt Internet commerce, merchants have to discover and assimilate the principles underlying Internet technologies, cyberculture, and cyberspace economics. Only by building on that appreciation will they be able to devise principles and practices that match consumers' expectations and needs, and thereby fulfil the marketer's own objectives.
To apply the decision model within this context demands that the consumer view be examined first. The preparedness of consumers to spend money has not died, because cyberculture ethos is not exclusively about gratis access to everything. But the motivators for consumers go beyond brand, colour and excitement. Important among their requirements are straightforward offers; price, choice, and terms of trade that are transparent and fair; and risk-allocation that is both clear and favourable to consumers' interests.
The demotivators for consumers include perceived risk to their money, uncertainty about fulfilment and about product quality, complexity of process, risk to their data, and manipulation by merchants.
The motivators for merchants then need to be considered, and balanced against the requirements of consumers. There are many market segments in which a profit can be made from 'a fair deal', by structuring offers that are attractive to consumers, that share risks equitably, and that do not demand their identities and profiles. The demotivators for merchants are high infrastructure costs, and the contestability of customers who have no lock-in-based 'loyalty' to what used to be referred to as 'the incumbent supplier'. These are significant problems, but in many circumstances they are not insuperable ones.
The alternative approach perceives 'trust' very differently from conventional identity-based ideas. It is necessary to go back to the fundamental concept of trust, which is 'confident reliance by one party on the behaviour of others'. Its origins are in the mutual dependence inherent within familial, tribal and social settings.
When the term 'trust' is lifted out of its original context and used in discussions of Internet commerce, there are two major issues. One is that the social aspect fades and is more or less replaced by economic motivations; and the other is that the scale of the other party changes, from individuals and small groups to large, impersonal institutions.
As a result, trust in the context of consumer Internet commerce has little to do with mutual dependence. From the consumer's viewpoint, what online merchants means by it is merely 'the acceptance of the non-negotiable gap between what is desired and what is available'. It refers to the terms of trade and risk allocation that, through the use of their market power, merchants impose on individuals as a condition of the transaction (Clarke 2000).
The size of the gap is a major impediment to the adoption of consumer Internet commerce, and online merchants need to search for ways to reduce it. A starting-point is to recognise that a variety of approaches can be adopted, which have different degrees of strength. Exhibit 4 summarises the hierarchy, ranging from strong, relationship-based trust down to weak symbolism and imagery.
It is only natural that there is resistance to change, and that large consumer marketing organisations believe that they are, and that they should be, immune to change. There are myriad excuses for not accepting that an alternative approach is needed, not least that revolutions are rare, and that Internet commerce is a mere decade old. This section conducts a preliminary investigation as to whether one particular excuse is justified: that the alternative approach is impractical.
The implementation of cyber-aware consumer Internet commerce depends on the adoption of a set of principles. A revised version of those originally suggested in Clarke (1998) is in Exhibit 5.
The Fair Conditions principle requires that consumer protection be provided. Some approaches to consumer protection may be expensive for the merchant; but Exhibit 6 identifies many simple, inexpensive yet effective actions that can inculcate trust yet are all too rarely implemented.
A further cluster of positive measures can be undertaken in relation to risk management. The first aspect that attracts attention is financial risk. During the first few years, merchants were fairly well-protected against contingencies, because they used their market power to demand provision of credit-card details from consumers as a condition of doing business. The exceedingly low quality of the credit-card system has ceased to be an open secret, and is now well-known to large numbers of small-time thieves. As a result, chargeback ratios have increased, and in some industries credit-card fraud has reached epidemic proportions. See, for example, McCullagh (2003). Recent actions by credit-card scheme operators have been stop-gap measures that will have little effect, and a much more substantial security scheme needs to be developed very quickly. Identity authentication for consumers is a pipe-dream. On the other hand, a secure PIN-capture mechanism (which has the less ambitious effect of authenticating the assertion that the individual is authorised to use the card) would achieve a substantial reduction in fraud, and a shift back towards consumer responsibility for e-payments conducted using their card-details.
In addition to financial risk, consumers are concerned about many other categories, such as the quality of the tradeable item, and the quality of the fulfilment process. Further important factors are the policies, practices, and avenues for recourse in the event of malperformance. The Fair Conditions measures suggested earlier therefore need to be complemented by safeguards, such as warranties, escrow, industry and government complaints schemes that 'have teeth', insurance, and a credible insurer-of-last-resort.
Once these fundamental needs are addressed, it is very likely that privacy issues will emerge as a crucial impediment. This has already been evident in such data-sensitive markets as sex goods and banking. Undertakings by merchants will need to be much clearer and less dishonest. Jurisdictions that have to date avoided implementing privacy laws will need to enact at least 1970s-style legislation, in order to provide consumers with the necessary legal assurance (Clarke 1999a).
Marketers are still championing 'opt-out' notions. But consumers' demands for genuinely consensual 'opt-in' arrangements are much stronger than broadcast-era marketers appreciate. Strong evidence of this became available in mid-2003, when the pent-up demand for tele-marketing to be reined in was released by the establishment of the U.S. National Do Not Call register. The coming dominance of 'opt-in' leads to the need for mechanisms whereby eConsent can be expressed (Clarke 2002a).
In addition, the identity management notion needs to mature very rapidly if it is to make a useful contribution to the alternative approach to consumer marketing proposed in this paper. A critical requirement is nymity features, quite possibly at the level of anonymity, but at the very least at the level of robust pseudonymity (Clarke 1999b).
The conventional notion of 'marketing as conquest' does not and will not work in the new context. Marketers have to discover that the Internet is not a broadcast medium, that consumers have power (even if most of them haven't noticed it yet), and that buyers sitting at workstations are in a different mind-state from couch-potato TV-watchers. The problem with 'B2C' has always been the '2'. Merchants have to accept that there are two sides to the transaction, that broadcast is not how the primary Internet services work, and that rather than projecting at consumers, they have to work with them.
The argument presented in this paper might be interpreted as being anti-marketer and imbued with warm, fuzzy humanism. But it is actually rooted in pragmatism: Consumer Internet Commerce is growing far more slowly than it might, and merchants could achieve far more success if they went about their business differently.
Bambury P. (1998) 'A Taxonomy of Internet Commerce' First Monday 3, 10 (October 1998), at http://www.firstmonday.dk/issues/issue3_10/bambury/index.html
Bayers C. (1998) 'The Promise of One to One (A Love Story)' Wired 6.05 (May 1998), at http://www.wired.com/wired/archive/6.05/one_to_one.html
BBC (1998) 'Swoop on global Net paedophile ring ' BBC News Online: Sci/Tech, Wednesday, September 2, 1998, at http://news.bbc.co.uk/1/low/sci/tech/163017.stm
Benschop A. (2003) 'Internet Use(rs): Demography and Geography of the Internet', September 2003, at http://www2.fmg.uva.nl/sociosite/websoc/demography.html
Boutin P. (1998) 'Pushover?' Wired 6.03 (March 1998), at http://www.wired.com/wired/archive/6.03/updata.html?pg=1
Caruso D. (1996) 'Microsoft Morphs into a Media Company' Wired 4.06 (June 1996), at http://www.wired.com/wired/archive/4.06/microsoft_pr.html
Clarke R. (1998) 'Direct Marketing and Privacy' Xamax Consultancy Pty Ltd, 23 February 1998, at http://www.anu.edu.au/people/Roger.Clarke/DV/DirectMkting.html
Clarke R. (1999a) 'Internet Privacy Concerns Confirm the Case for Intervention' Communications of the ACM 42, 2 (February 1999) 60-67, at http://www.anu.edu.au/people/Roger.Clarke/DV/CACM99.html
Clarke R. (1999b) 'Identified, Anonymous and Pseudonymous Transactions: The Spectrum of Choice', Proc. User Identification & Privacy Protection Conf., Stockholm, 14-15 June 1999, at http://www.anu.edu.au/people/Roger.Clarke/DV/UIPP99.html
Clarke R. (2000) 'Trust in the Context of e-Business', Xamax Consultancy Pty Ltd, July 2000, republished in Internet Law Bulletin 4, 5 (February 2002) 56-59, at http://www.anu.edu.au/people/Roger.Clarke/EC/Trust.html
Clarke R. (2001a) ''Meta-Brands'' Privacy Law & Policy Reporter 7, 11 (May 2001), at http://www.anu.edu.au/people/Roger.Clarke/DV/MetaBrands.html
Clarke R. (2001b) 'Paradise Gained, Paradise Re-lost: How the Internet is being Changed from a Means of Liberation to a Tool of Authoritarianism' Mots Pluriels 18 (August 2001), at http://www.anu.edu.au/people/Roger.Clarke/II/PGPR01.html
Clarke R. (2002a) 'e-Consent: A Critical Element of Trust in e-Business' Proc. 15th Bled Electronic Commerce Conf., Bled, Slovenia, June 2002, at http://www.anu.edu.au/people/Roger.Clarke/EC/eConsent.html
Clarke R. (2002b) 'The Birth of Web Commerce' October 2002, at http://www.anu.edu.au/people/Roger.Clarke/II/WCBirth.html
Clarke R., Dempsey G., Ooi C.N. & O'Connor R.F. (1998) 'Technological Aspects of Internet Crime Prevention' Proc. Austral. Inst. for Criminology Conf. on 'Internet Crime', February 1998, at http://www.anu.edu.au/people/Roger.Clarke/II/ICrimPrev.html
Clarke R. & Nees S. (1999) 'Technological Protections for Digital Copyright Objects' Proc. 8th Euro. Conf. Infor. Sys. (ECIS'2000), July 2000, pp. 745-752, at http://www.anu.edu.au/people/Roger.Clarke/II/TPDCO.html
DMA (2002) 'Privacy Promise Member Compliance Guide', The Direct Marketing Association, revision of July 2002, at http://www.the-dma.org/privacy/privacypromise.shtml
Economides N. (1996) 'The Economics of Networks' Int'l J. of Industrial Organization, 14, 2 (March 1996), at http://raven.stern.nyu.edu/networks/94-24ps.zip
EPIC (2000-) 'Sign Out of Passport!' Electronic Privacy Information Center, at http://www.epic.org/privacy/consumer/microsoft/default.html
EPIC (2002-) 'Digital Rights Management and Privacy' Electronic Privacy Information Center, at http://www.epic.org/privacy/drm/default.html
Ghosh R.A. (1998) 'Cooking pot markets: an economic model for the trade in free goods and services on the Internet' First Monday 3 3 (March 1998), at http://www.firstmonday.dk/issues/issue3_3/ghosh/index.html
Hauben M. & Hauben R. (1997) 'Netizens : On the History and Impact of Usenet and the Internet' IEEE Computer Society; ISBN: 0818677066, 1997, also at http://www.firstmonday.dk/issues/issue3_7/index.html
Hiltz S.R. & Turoff M. (1993) 'The Network Nation: Human Communication Via Computer' MIT Press, 1993
Hoffman D.L. (2003) 'The Consumer Experience: A Research Agenda Going Forward', PowerPoint slides for an FTC Workshop on Technologies for Protecting Personal Information: The Consumer Experience, Vanderbilt University, May 2003, at http://elab.vanderbilt.edu/research/papers/ppt/FTC.privacy.ppt
Hoffman D.L. & Novak T.P. (1997) 'A New Marketing Paradigm for Electronic Commerce', The Information Society, Special Issue on Electronic Commerce, 13 (Jan-Mar.), 43-54, earlier version at http://elab.vanderbilt.edu/research/papers/html/manuscripts/new.marketing.paradigm.html
Kelly K. (1997) 'New Rules for the New Economy', Wired 5.09 (September 1997), at http://www.wired.com/wired/archive/5.09/newrules.html
Kelly K. & Wolf T. (1997) 'Push! Kiss your browser goodbye: The radical future of media beyond the Web', Wired 5.03 (March 1997), at http://www.wired.com/wired/archive/5.03/ff_push_pr.html
Kollock P. & Smith M. (1999) 'Communities in Cyberspace' University of California, Los Angeles, 1999, at http://www.sscnet.ucla.edu/soc/faculty/kollock/papers/communities_01.htm
Lamberton D.M. (Ed.) (1971) 'The Economics of Information and Knowledge' Penguin 1971
Lamberton D.M. (Ed.) (1996) 'The Economics of Communication and Information' Edward Elgar, 1996
McCullagh D, (2003) 'Study: Millions hit by ID fraud', ZDNet, September 04, 2003, at http://www.zdnet.com.au/printfriendly?AT=2000048600-20278181
Madsen H. (1996) 'Reclaim the Deadzone' Wired 4.12 (December 1996), at http://www.wired.com/wired/archive/4.12/esmadsen_pr.html
Nee E. (1998) 'Welcome to my store ' Forbes, October 19, 1998, at http://www.forbes.com/forbes/98/1019/6209140a.htm
NOIE (2003) 'NOIE Information Economy Index' National Office for the Information Economy, Canberra, Australia, August 2003, at http://www.noie.gov.au/publications/NOIE/NOIE_index/Aug03/ebusiness.htm#19
Nollinger M. (1995) 'America, Online!' Wired 3.09 (September 1995), at http://www.wired.com/wired/archive/3.09/aol.html
NUA (2002) 'How Many Online?', NUA Internet Surveys, at http://www.nua.ie/surveys/how_many_online/index.html
NUA (2003) 'U.S. E-Commerce 1998-2003', NUA Internet Surveys, at http://www.nua.com/surveys/analysis/graphs_charts/comparisons/ecommerce_us.html
Olsen S. (2002) 'DoubleClick turns away from ad profiles' CNet, 8 January 2002, at http://news.com.com/2100-1023-803593.html?legacy=cnet
Peppers D. & Rogers M. (1993) 'The One to One Future : Building Relationships One Customer at a Time', Doubleday, 1993
Pew (2003) 'The Ever-Shifting Internet Population: A new look at Internet access and the digital divide' Pew Research Center, April 16, 2003, at http://www.pewinternet.org/reports/reports.asp?Report=88&Section=ReportLevel1&Field=Level1ID&ID=378
PRB (2003) '2002 World Population Data Sheet', Population Reference Bureau, at http://www.prb.org/Content/ContentGroups/Datasheets/wpds2002/2002_World_Population_Data_Sheet.htm
Rappa M. (2003) 'Business Models on the Web', at http://digitalenterprise.org/models/models.html
Rappa M. (2003) 'Trust in Cyberspace', at http://digitalenterprise.org/trust/trust.html
Raymond E.E. (1998) 'The Cathedral and the Bazaar' First Monday 3 3 (March 1998), at http://www.firstmonday.dk/issues/issue3_3/raymond/index.html
Rheingold H. (1994) 'The Virtual Community in a Computerized World' Secker & Warburg 1994, at http://www.rheingold.com/vc/book/
Schrage M. (1994) 'Is Advertising Dead?' Wired 2.02 (February 1994), at http://www.wired.com/wired/archive/2.02/advertising_pr.html
Shapiro C. & Varian H.R. (1999), 'Information Rules' Harvard Business School Press, 1999, at http://www.inforules.com/
Thornberry K. (1998) 'Web search engines get personal: `Start pages' deliver info to Internet users', Business Courier, 19 October 1998, at http://www.amcity.com/cincinnati/stories/101998/focus7.html
TNSG (2002) 'Glocal eCommerce Report - 2002', Taylor Nielsen Sofres Global, 2002, at http://www.tnsofres.com/ger2002/home.cfm
Voight J. (1996) 'Beyond the Banner' Wired 4.12 (December 1996), at http://www.wired.com/wired/archive/4.12/esadvertising_pr.html
Winner L. (1991) 'Victory for Computer Populism' Technology Review, September 1991
Wired News (2003) 'RIAA Goes After the Wrong Gal' Wired News, 24 September 2003, at http://www.wired.com/news/digiwood/0,1412,60581,00.html
Wolfe G. (1994) 'The (Second Phase of the) Revolution Has Begun' Wired 2.10 (October 1994), at http://www.wired.com/wired/archive/2.10/mosaic.html
Go to Roger's Home Page.
Go to the contents-page for this segment.
Created: 17 November 2003
Last Amended: 9 December 2003
 | These community service pages are a joint offering of the Australian National University (which provides the infrastructure), and Roger Clarke (who provides the content). |  |
| The Australian National University Visiting Fellow, Faculty of Engineering and Information Technology, Information Sciences Building Room 211 | Xamax Consultancy
Pty Ltd, ACN: 002 360 456 78 Sidaway St Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 1472, 6288 6916 |