Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
PrePrint of 11 February 2014
Published in Proc. Bled eConference, June 2014
Version also published in Organizacija 47, 4 (2014) 219-230
© Xamax Consultancy Pty Ltd, 2012-14
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/II/COSM-1402.html
The supporting slide-set is at http://www.rogerclarke.com/II/COSM-1402.pdf
The term 'social media' refers to a cluster of applications and online services that support human interaction and content broadcasting and sharing. Current services are isolated islands or 'walled gardens', and are based on a business model that is highly exploitative of individuals and their data. An alternative, consumer-oriented approach is feasible, involving open architecture, inter-operability and portability features, fair terms and privacy-sensitivity. Key impediments to the emergence of such services are identified, and means of overcoming the impediments are outlined.
Social media is a collective term for a range of services that support users in interacting with one another, and in exchanging content and pointers to content. Some social media services have proven to be short-lived fads. Some appear to be instances of longer-lived genres, although, even in these cases, waves of specific services have been crashing over one another in quick succession. Some aspects may mature into long-term features of future services, because they satisfy a deeper human need rather than just a fashion-driven desire. At any given time, which services belong in which of those categories is hotly-debated and highly unclear. During the first decade, 2004-14, social media has been a cauldron of innovation and early death. See, for example, the Wikipedia 'graveyard lists' of discontinued social networking sites, photo-sharing sites, video-sharing sites, and Google services.
Social media services have stimulated a revival of the aura of excitement that preceded the dot.com boom c. 2000. Many have had no discernible business model beyond the presumption that 'there must be a way to monetise this somehow'. Successful services, however, are predicated on what is referred to in this paper as'the exploitative business model', and described in s.2.2 below. An epithet commonly applied to it is 'If you're not paying, you're the product' (e.g. Schneier in Shane 2010).
A proportion of users understand that they are being exploited by social media service providers. The boldness and even arrogance of many of those providers have given rise to a growing body of utterances by influential commentators, which has caused a lot more users to become aware of the extent of the exploitation. Consumer and privacy issues are legion, and give rise to doubts about whether sufficient trust exists to sustain the momentum achieved during the first decade of social media usage.
The research reported on in this paper was motivated by the need to move beyond mere criticism of existing social media services,. The research builds on a substantial prior program of research and publication in related areas, which has given rise to a dozen refereed papers over the last decade. The research question that this project sought an answer to was 'How can consumer-oriented social media be achieved?'. This was decomposed into the following sub-questions:
Surveys of the refereed literature have been undertaken on several occasions during the period 2012-13. Despite the vast amount published on social media, the aspects being considered here are not yet an established field of research. The majority of social science and business literature works within the industry's existing frame of reference, rather than questioning its underlying assumptions. In more technical areas, on the other hand, a limited literature exists.
Surveys were conducted of social media services that are reasonably described as 'consumer-oriented'. A moderate number have been conceived, and some have been launched; but none appear to have reached a critical mass of users or traffic. In order to complement the limited relevant literature and empirical base, surveys were also undertaken of media reports. This is particularly important in a field that is so highly dynamic and where a lag of 2-3 years exists between developments occurring and refereed articles being published that examine those developments.
The available information was then subjected to analysis, including reflection based on prior research conducted by the author. This enabled the identification of required characteristics of consumer-oriented social media, and of barriers to emergence and adoption of such services. That provided a basis for the postulation of means to overcome those barriers.
The following section examines the nature of social media and distinguishes genres. This leads to the identification of five clusters of characteristics that would together deliver an appropriate orientation towards consumer needs. Key impediments that have held back the emergence of such services are then outlined, and possible means of overcoming them are presented.
This section reviews the origins and nature of social media services, and proposes a classification scheme for service-features. It also considers the means whereby service-providers fund their operations. Consideration is also given to the adaptation to the mobile context that is currently in train, which involves increasing location-awareness among social media services.
Searches for formal literature that uses the term 'social media' in the relevant way have uncovered very little prior to 2004. Even the term 'social networking' only emerged about that time - although there is a prior literature on the notion of 'social networks' (e.g. Rheingold 1993, Wilde & Swatman 1999). The 'social media' meme emerged in conjunction with the 'Web 2.0' notion, during 2004-05 (O'Reilly 2005). As shown by Clarke (2008b), there was little terminological clarity or coherence during the first several years of discussion of the approaches adopted by marketers during this period.
Even in 2010, the available definitions remained primitive, e.g. "Social Media is a group of Internet-based applications that build on the ideological and technological foundations of Web 2.0, and that allow the creation and exchange of User Generated Content" (Kaplan & Haenlein 2010, p.61). Those authors did, however, apply theories in the field of media research (social presence, media richness) and social processes (self-presentation, self-disclosure), in order to propose the classification scheme in Table 1.

The Kaplan & Haenlein classification scheme is a good fit to the perspectives of corporations. On the other hand, through its commitment to the mass-marketing, 'consumer as prey' tradition, it fails to adequately reflect the interests of the users who social media exploit. A classification scheme was accordingly sought that is oriented towards the interests of the users of social media.
No appropriate model came to light in the literature. The approach adopted was therefore to search for and inspect lists of services described as social media, and identify their key characteristics from a user's perspective. During the process, reference was made to a related scheme developed two decades earlier in Clarke (1994). This included a large number of the concepts evident in the 'social media' cluster. Ideas that were not evident two decades ago were glogs, wikis, crowdsourcing, folksonomies, indicator-sharing, and high-quality animation and hence avatars. The classification scheme arising from that study is depicted in Table 2. It is based on two factors: the cardinality of the relationship among the parties, and the nature of the exchange.
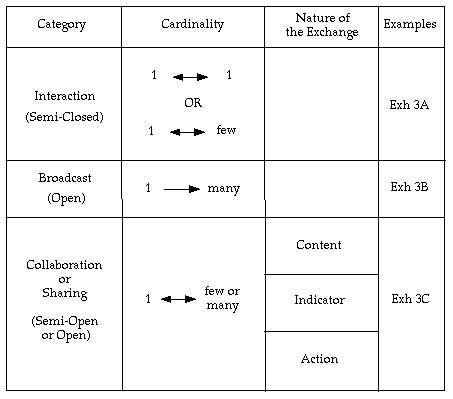
Within each of the major categories, a variety of tools are available. These differ in terms of the a/synchronicity of the communications, the nature of the exchange - including syntactic aspects such as whether it comprises text, sound, image and/or video, and semantic aspects such as the implications of the content - and the key functionality that they offer. Some are inter-personal messaging tools, whereas others are content-publishing tools - many of which also offer content-preparation functionality. Some are applications of 'crowdsourcing' (Howe 2006), enabling large-scale aggregation of, in some cases, substantial content (e.g. Wikipedia), but in many cases much more limited signals such as declarations of approval or disapproval, or actions in an online game.
Appendices 1, 2 and 3 present the currently-available service-genres in the approximately chronological order in which they emerged, together with examples of each genre. The classification scheme provided in Table 2 and the Appendices distinguishes functions. A great many social media services - especially those that have survived longer than 1-2 years - have adapted and expanded, and hence offer multiple functions. Any given social media service may therefore appear as an example in multiple categories.
The term 'business model' refers to "a description of the value a company offers to one or several segments of customers and the architecture of the firm and its network of partners for creating, marketing and delivering this value and relationship capital, in order to generate profitable and sustainable revenue streams ... the missing link between strategy and business processes" (Osterwalder & Pigneur 2002), or "the method of doing business by which a company can sustain itself -- that is, generate revenue" (Rappa 2003). Rappa went further, by distinguishing a set of categories, comprising Brokerage, Advertising, Infomediary, Merchant, Manufacturer (Direct), Affiliate, Community, Subscription and Utility. A useful simplification that has been applied in a variety of eBusiness contexts is that a business model is the answer to the question 'Who pays, for what, to whom, and why?" (Clarke 2004b). The categories in Bambury (1998) have a close fit to that form.
The earliest reference on business models for social media is usually regarded as being O'Reilly (2005). The widespread understanding is that "social networking sites can generate revenues through advertising, subscription, and transaction models" (Enders et al. 2008). More specifically, several variants of the advertising agency business model are applied, which involve renting out space on pages on web-sites, usefully referred to as an 'advertising syndication' approach (Clarke 2008b, s. 4.2). The model's downsides for consumers is discussed in s.4.2 below.
Marketer enthusiasm for so-called 'Web 2.0' business models has attracted criticism, e.g. "We need to carefully dismantle the claims of Wikinomics, `We-Think' and Convergence Culture in order to better understand the kind of brave new worlds to which we are being welcomed" (van Dijck & Nieborg 2009), and "[business models for] monolithic, company-owned social networking websites ... are generally based on gathering, using, and monetizing data about you" (Esguerra 2011).
More specifically, the model depends on the following propositions:
Mainstream, exploitative social media service providers have available to them the profile-data that each individual has supplied, the content that they have posted - whether publicly or 'privately', their online behaviour while using the service, in some cases their online behaviour more generally, plus the information disclosed by other users about them.
In addition to the manipulation of consumer behaviour that is inherent in targeted advertising, substantial privacy intrusions arise, and so do freedom of expression issues: "The social networking company might cause you to overshare information that you don't want shared, or might disclose your information to advertisers or the government, harming your privacy. And conversely, the company may force you to undershare by deleting your profile, or censoring information that you want to see make it out into the world, ultimately curbing your freedom of expression online. And because the company may do this, governments might attempt to require them to do it, sometimes even without asking or informing the end-user" (Esguerra 2011).
As is evident from the early dates in Appendices 1-3, the origins of all categories of social media service are in the era of desktops and laptops. The mobile age of smartphones and tablets has been accompanied by a variety of ways in which devices, and hence their users, can be located and tracked (Michael & Clarke 2013).
Throughout the network-based telecommunications era, each person's network address has always been visible, as a necessary element of the services. Since around the turn of the century, however, each person's physical address, or geo-location, has progressively become available, and in the case of cellular phone networks knowledge of the geo-location of a device is intrinsic to the operation of the infrastructure. This has enabled a variety of location-based services. Some of them are much-appreciated by consumers, such as those that provide navigation assistance, and assist in emergencies. Novelty apps have attracted attention, such as notification services when someone in the person's address-book is in their vicinity.
However, all such services, whether appreciated by the user or not, gift rich streams of personal data to service-providers. The primary use of geo-location is in consumer marketing. A further major application of person-location and tracking capabilities is law enforcement and national security (Clarke 1999b, Clarke & Wigan 2011, Michael & Clarke 2013).
A few recently-emerged social media services are 'born mobile', with geo-location intrinsic to their design. Foursquare is a high-profile example. The challenges that these new entrants posed to established players was so great that they adopted anti-competitive methods, with Dodgeball acquired by Google and closed down, and Gowalla purchased by Facebook and abruptly killed. However, during 2013, Google closed down its interim Latitude service in favour of partially-integrated features within Google+, and Facebook declared itself to be in transition to a much stronger orientation towards mobile users (Womack 2013). Despite the enormous privacy-sensitivity of location data to a wide variety of user-categories, all major social media service-providers encourage disclosure, and have very lax privacy controls.
The social media services that emerged during 2004-2010 benefited from what transpired to be massive user enthusiasm for the services' mix of voyeurism and exhibitionism, and the thrill of being 'connected' with 'friends'. The widespread and rapid adoption brought with it a range of problems. Concern has been increasingly evident among commentators, and increasingly among users as well (e.g. Opsahl 2010, O'Connor 2012).
There is a considerable lag before critical articles appear in the refereed literature. For example, in the Bled Proceedings, 'social networking' appeared for the first time only in 2008 - 4 years after the term entered mainstream use - and during 2009-13 the term appeared in the Abstract of only 12 papers (5.5%). The phrase 'social media' first appeared only in 2010, with 13 papers during 2010-13 using it in the Abstract (7.8%). Mentions in the text, however, were consecutively 6, 11, 20 and 15 (i.e. 33% of all papers during that period).
A review of the above Bled papers found that all adopted a business perspective, and none addressed the topic focussed on in the present paper. In order to supplement the limited academic literature, articles in the technical media have been used. In addition, a review was undertaken of the considerable number of tools, prototypes and services that have emerged that are intended to be, or are at least projected as being, consumer-friendly. The origins of those projects vary, but an important stimulus has been the desire for tools for communication and collaboration among groups that perceive themselves to be under threat from governments or corporations.
Table 3 presents a list of relevant services, drawn from the formal literature and the media of the period since 2005. The field has featured a scatter of many, small initiatives, and hence an exhaustive list is infeasible. The list is, however, reasonably comprehensive. There are very substantial differences among the projects in the list. Some are user-facing, whereas others are infrastructural in nature; some are operational, whereas others are 'in beta', and some are merely aspirational; and some are related to mainstream commercial products, whereas others expressly blend social with economic objectives, and others are inherently counter-cultural.
An indication of the level of academic interest in these initiatives is provided by searches in Google Scholar. The most prominent of the services is Table 3 is Diaspora* (Bleicher 2011, Cox 2013 pp. 60-80). Diaspora* has been addressed in very few academic papers, however, and very few of the papers that mention it have more than a handful of citations. It appears that StatusNet has recently been attracting some attention, in particular as infrastructure over which research experiments can be performed.
An indicator of the level of use of these services can be gained from Wikipedia catalogues. Some, but by no means all of them, appear in the Wikipedia Comparison of software and protocols for distributed social networking. On the other hand, in February 2014, the Wikipedia catalogue of social networking sites identified only two as having a substantial user-base - Diaspora and identi.ca, each with a little under 400,000 users. Of the other 16 services listed in Table 3, only Friendica even appeared in the catalogue. The catalogue contained 100 services whose user-base was claimed to be in excess of 400,000. Each of the top 60 was shown as having in excess of 5 million users, and their total user-count was shown as 5.5 billion. If those numbers were treated as being authoritative, the users of existing consumer-oriented social media would appear to number of the order of 0.01% of the total social networking services user-base.
The following section utilises the sources discussed above to identify key features of consumer-oriented social media. The subsequent sections then turn to the question of why these services are being used by so few people, and what can be done about the impediments to adoption.
There are five broad areas in which features of existing social media services are at least unsatisfactory in terms of their fit to consumers' needs, and are arguably seriously detrimental to consumers' interests. These areas are:
The following sub-sections consider each in turn.
Almost all services to date have used client-server architecture, which provides the service-provider with control over the individual's content. A fully peer-to-peer (P2P) architecture, on the other hand, leaves that control in each individual's hands. Alternatively, and perhaps more practicably in large-scale applications, semi-P2P architectures distribute content and control across many participant-controlled devices and thereby greatly reduce the power of the service-provider over the users' data. Narayanan et al. (2012) examines characteristics of distributed architectures for social networking.
The following summary of the argument appears in Moglen (2010):
" ... if you have a system which centralizes servers and the servers centralize their logs, then you are creating vast repositories of hierarchically organized data about people ... that they do not control and ... will not understand the comprehensiveness of, the meaningfulness of, ... the aggregatability of.
" ... we built a network out of a communications architecture design for peering which we defined in client-server style, which we then defined to be the dis-empowered client at the edge and the server in the middle. We aggregated processing and storage increasingly in the middle and we kept the logs ... in centralized places far from the human beings who controlled or thought they controlled the operation of the computers that increasingly dominated their lives. This was a recipe for disaster.
"We need to re-architect services in the Net. We need to re-distribute services back towards the edge. We need to de-virtualize the servers where your life is stored and we need to restore some autonomy to you as the owner of the server ... This is technical challenge for social reason"
"We need a really good webserver you can put in your pocket and plug in any place ... a freedom box".
Inspired by Moglen, and fuelled by one of the many rounds of privacy-invasive behaviour by Facebook, Diaspora implemented a distributed architecture (Musiani 2010, Franchi & Tomaiuolo 2012). Indeed, the name implies it, because 'disapora'means dispersion or scattering. A user may install a 'pod' (server) on their own device, or may instead use a 'community pod'. A pitch by the Diaspora* team ran "In real life we talk to each other. We don't need to hand our messages to a hub and have them hand it to our friends. Our virtual lives should work the same way" (Bleicher 2011, p. 50).
Most services have worked very hard to capture their users within a 'walled garden', with pages pasted on the inside wall and denied to outsiders, and users' interactions trapped inside the service-provider's proprietary messaging scheme. The originator of the Web has criticised this approach for many years, e.g. Cox (2007). He has summarised the problem as follows: "closed, 'walled gardens', no matter how pleasing, can never compete in diversity, richness and innovation with the mad, throbbing Web market outside their gates. If a walled garden has too tight a hold on a market, however, it can delay that outside growth" (Berners-Lee 2010, p. 83).
In a consumer-friendly design, not only does the user determine the degree of openness, but the content and messages are open to other people who the user authorises, irrespective of whether those people are connected to, or even members of, that user's service-provider. This requires the use of open protocols such as http and smtp/pop/imap and/or associated open standards for inter-operation among multiple services. A model of interoperable social media architecture is in Yeung et al. (2009), an outline of the 'federated social network' notion is in Esguerra (2011), and further discussion and a case study are in Cabello et al. (2013).
All forms of interoperability are naturally opposed by those with dominant market-shares, because it reduces the exclusivity, and hence the value, of their 'walled gardens', increases customer 'churn', increases the cost of acquiring and retaining customers, and shifts power back towards consumers.
Existing services not only trap a user's profile-data, messages and content inside the provider's walled garden, but also provide inadequate means for it to be rescued and transferred across into an alternative environment. A limited exception is Google, which supports export of some forms of data from a small number of Google services by means of its Takeout Product.
Portability is vital to enable user choice. This is not merely a social argument, because it is well-grounded in economics. Monopoly prevents the efficient use of resources. Competition is crucial, and competition depends heavily on 'switching costs' being low. If social media users cannot extract their content and postings, the costs of switching from one service-provider to another include the abandonment of their entire archive.
The contract between users and the service-provider is dictated by the Terms of Service imposed by that organisation. Previous research has identified a substantial set of problems from the perspective of consumers, across the entire range of consumer protection areas (Clarke 2008a, Svantesson & Clarke 2010, Clarke 2010a, 2010b, 2011).
A 'Bill of Rights for Users of the Social Web' (Smarr et al. 2007) asserted rights of ownership (whatever that might mean in the context of data), control of whether and how much personal data is shared with others, and the 'freedom to grant access' to personal data. This fell a long way short of being an effective or a sufficient formulation from the viewpoint of consumer rights, however. An alternative and somewhat more workable formulation, arising from a session of the Computers, Freedom & Privacy Conference (CFP 2010), is reproduced in Table 4. Another expression of users' requirements is in Exhibit 4 of Clarke (2011).
There has been, and continues to be, a great deal of abuse by social media service-providers of their users' privacy (Handel 2011), and a great deal of media coverage has resulted. There have been claims that privacy norms and laws need to be adapted to reflect the circumstances of social media. For example, Cox (2013, pp. 81-82) refers to data protection, as that term is implemented in Fair Information Practices instruments, as 'institutional privacy', and identifies additional needs, referred to as 'social privacy' relating to the unintended or otherwise inappropriate re-posting of personal data. A deeper assessment is in s.2 of Clarke (2014), and a catalogue of specific issues is provided in a companion Working Paper arising from this research project, in s.4.3 of Clarke (2013).
Existing services offer a variety of features that address particular aspects of the privacy-intrusiveness of exploitative social media. For example, Diaspora* incorporates the scope to operate isolated sub-services run on a local server (or 'pod'), better control over groups (called 'aspects'), recoverability of postings, and specific support for pseudonyms.
There is a degree of clarity about the appropriate features of consumer-oriented social media, and a considerable number of projects have been commenced to deliver services with various sub-sets of those features. A proportion of those services have been launched, yet very few have significant numbers of users. This section draws on the results of the analysis to identify what appear to be the key impediments.
One of the few teams to have addressed this question identified the following reasons for the delay in the emergence of 'free Social Networking Services': "a lack of material and economic resources; a lack of interest in what many considered to be a teen fad with little potential for the self-organization of civil society; or the inability of social movements to capitalize and innovate on the fundamental principles they practice within cyberspace: participation, horizontality and collective intelligence" (Cabello et al. 2013). This section identifies the following factors:
Adoption of a category of services is predicated on the existence of factors that drive users to those services. Effective demand is dependent on a number of pre-conditions, such as awareness, perceived benefits and perceived advantage. It would require empirical research to confirm, but the strong probability is that relatively few users would currently adopt such services even if they were aware of them. There is a lack of understanding of the problems with existing services, and of the availability of alternatives. There are also strong counter-drivers, because existing services are designed to be compelling, to serve individuals' hedonistic needs, to fit with whatever passes for fashion at the time, and to fit conveniently with individuals' life-patterns.
A further, important factor is that the network effects involved in social media favour incumbents. As long as the small number of services that have achieved dominant market-share remain closed, 'walled gardens' - by denying interoperability and portability - new entrants, both those that are conventionlly exploitative and those that are consumer-friendly, are unable to achieve penetration.
Although the closedness of the dominant social media providers is a major factor, so too is the success of their business model. Research is needed into the keys to that success. It appears to be a combination of marketing and design that targets individuals' hedonist impulses and the current penchant for self-exposure and outright exhibitionism, linked with the super-profits that arise from monopoly, and the over-valuation and consequential high capital-raising capabilities that arise from the prospect of super-profits.
A deeper appreciation of the conventional model can be informative to endeavours to develop, promote and sustain services without exploiting personal data in ways that conflict with user's needs and reasonable expectations.
Diaspora* and similar services have suffered from the same problem as most other software developed over the last one to two decades. Software development is dominated by quick-and-dirty coding methods, glorified as 'rapid application development', which features the substantial absence of requirements statements, architectural frameworks, and design specifications. This results in a high incidence of design errors, the continual emergence of security vulnerabilities, instability in architecture, and unpredictability of the scope of bug-fixes and changes.
Commercial enterprises that are suitably capitalised and/or achieve substantial revenue flows can limp along for many years, coping with low software quality by throwing resources at the problems. Suppliers of consumer-oriented social media have to date lacked large-scale funding, are unable to buy their way out of software quality problems, and hence the service-quality problems remain, fester, damage customer loyalty, and result in drift of users away from the site, which leads to negative network effects, decline, and death.
With only rare exceptions, consumer-oriented social media have been developed using tools that are to hand, rather than tools that have been carefully selected to fit the need. Services developed using such tools seldom run efficiently. Those services that achieve significant adoption quickly run into the problem that demand grows exponentially, and the service's inefficient back-end software and data management cannot support it.
It is common for successful services to be in a state of continual redevelopment, including frequent upgrading or replacement of infrastructure, in order to keep the service running as increasing numbers of users adopt it. This requires significant levels of funding, which are often not available to most providers of consumer-oriented social media. As a result, users suffer slow service, customer loyalty is affected, users drift away, and success breeds failure.
For the impediments identified in the previous section to be overcome, it appears that three sets of measures are necessary. Designs need to address needs, public understanding needs to be much-enhanced, and alternative business models need to be articulated and implemented, sufficient to support professional levels of quality and scalability.
In order to project themselves as consumer-oriented, service-providers need to exclude the features that are associated with exploitation, and incorporate a sufficient sub-set of the features described in section 4 above. Interoperability and portability are highly advisable features. If a distributed architecture is not included, then a much larger sub-set of consumer-friendly terms of service and privacy features is likely to be needed.
Academics and some of the more thoughtful media commentators have documented the negative aspects of exploitative social media, and the harm that they embody. But intellectual discourse has little impact in the marketplace. Adoption of consumer-oriented social media depends on users feeling the difference, and hearing and seeing the messages, in language that relates to their worlds, and conveyed by people who they regard as influencers.
Key aspects of marketing communications theory and practice need to be applied, in order to achieve 'mindshare' among target audiences, and among channels to those target audiences. Media are to a considerable extent regurgitators of media releases. Promoters of consumer-friendly social media services need to project themselves as organisations of substance, and present their case in forms that fit to the channels' self-image and formats, and that reflect the fashions of the moment. It is essential to be ready to leverage off the public relations disasters that exploitative social media continually create for themselves. In effect, promotions need to be 'in the can', ready to launch, when an opportunity presents itself.
A new service needs to launch with a critical mass of features, with a user interface that is better than merely adequate, with service-quality comparable to that of existing services, and with the capacity to scale with demand, and to fix bugs, add features, and adapt interfaces (and even offer alternative interfaces). That requires a sufficient investment prior to launch, and a sufficient set of resources during the ramp-up phase.
Many alternative business models are available, well beyond what this paper has referred to as the exploitative model that dominates contemporary social media services. A framework was provided by Exhibit 4 of Clarke (2004b), comprising answers to the questions 'Who pays? What for? To whom? and Why?'. The application of the framework to 'content commons' was documented in Clarke (2007). Examples provided in those articles and the sources that they reference include government support for services that fulfil their mission statements, government subsidies, corporate cross-subsidies (i.e. business enterprises supporting loss-making services that are complementary to their other products and services), sponsorship and patronage e.g. by philanthropic and religious organisations, advertising that offers less-precisely-targeted placements for lower costs than exploitative outlets, and subscription fees for value-added services such as 'vanity press' blogs.
As the benefits of consumer-friendly social media become more widely understood, some mainstream commercial providers may be tempted into the field - particularly those that are unable to gain sufficient market-share to reap monopoly profits. For example, the prospect exists of corporations that sell 'enterprise' products and services, such as Yammer, supporting gratis open services as a viral marketing channel, promoting the brand and associating a 'feel-good' factor with it.
Naturally, as alternative approaches begin to represent a threat to powerful corporations, countermeasures will be adopted as they seek to protect or at least prolong their monopolies. Because of the scale these organisations have achieved, their economic power over Congress, and their surveillance significance to the US Administration, the companies will be able to enlist government support for their stifling of competitors.
Searches have already been undertaken for middle paths, whereby corporations' ability to exploit data can be sustained, while users' control is improved and at least some of the more extreme privacy incursions are reduced. For example, Wilson et al. (2011) proposed "a distributed OSN architecture that significantly improves user privacy while preserving economic incentives for OSN providers ... by using a standardized API to create a competitive provider marketplace for different components of the OSN, thus allowing users to perform their own tradeoffs between cost, performance, and privacy". However, their Polaris architecture is based on the spurious notion that privacy concerns only arise in relation to a few specific data-items, and that all other data can remain free for exploitation. Other such pseudo-solutions that sustain the dominance of the exploitative business model are bound to emerge.
Consumer-oriented social media services are needed, as an antidote to the exploitative approach adopted by providers during their first decade. Public understanding of the nature of existing social media services appears to be increasing. The dominant service-providers, particularly Facebook and Google, show no signs of reducing the exploitative nature of their business models, and hence it appears likely that the proportion of the customer-base that will seek alternatives will increase. A key question is how consumer-oriented social media services will come into being, and survive long enough, to establish critical mass. The research reported on in this paper has consolidated the information available in the area, and identified the articulation of alternative business models as the single most important factor that will determine ventures' success or failure.
Opportunities for research present themselves in relation to the ease of delivery of infrastructure, adaptability and scalability. Social science research is needed in order to determine the trade-offs among various features. Surveys provide data of only limited quality, and controlled experiments appear to be a much more promising technique. Deep case studies are needed of successful and failed projects. Relevant information generated by well-conceived instrumentalist research could make valuable contributions to overcoming the impediments that have held back the emergence of consumer-friendly social media.
Bambury P. (1998) 'A Taxonomy of Internet Commerce' First Monday 3, 10 (October 5, 1998), at http://www.firstmonday.dk/issues/issue3_10/bambury/index.html
Bankston K. (2009) 'Facebook's New Privacy Changes: The Good, The Bad, and The Ugly' Electronic Frontier Foundation, 9 December 2009, at https://www.eff.org/deeplinks/2009/12/facebooks-new-privacy-changes-good-bad-and-ugly
Barnes S.B. 'A privacy paradox: Social networking in the United States' First Monday 11, 9 (September 2006), at http://firstmonday.org/htbin/cgiwrap/bin/ojs/index.php/fm/article/viewArticle/1394/1312%23
BBC (2011) 'Facebook U-turns on phone and address data sharing' BBC News, 18 January 2011, at http://www.bbc.com/news/technology-12214628
Bell E. (2012) 'The real threat to the open web lies with the opaque elite who run it' The Guardian, 16 April 2012, at http://www.guardian.co.uk/commentisfree/2012/apr/16/threat-open-web-opaque-elite
Berners-Lee T. (2010) 'Long Live the Web' Sci. Am. December 2010, pp. 80-85, at http://www.cs.virginia.edu/~robins/Long_Live_the_Web.pdf
Bettini C., Jajodia S., Samarati P. & Wang X.S. (Eds.) (2009) 'Privacy in Location-Based Applications: Research Issues and Emerging Trends' Lecture Notes in Computer Science 5599, Springer-Verlag, 2009
Bleicher A. (2011) 'The Anti-Facebook' IEEE Spectrum, June 2011, pp. 47-51, 74, at http://www.arielbleicher.com/Docs/Diaspora.pdf
boyd d. (2008) 'Facebook's Privacy Trainwreck: Exposure, Invasion, and Social Convergence' Convergence: The International Journal of Research into New Media Technologies 14, 1 (2008) 13-20
boyd d. (2012) 'The politics of "real names"' Communications of the ACM 55, 8 (August 2012) 29-31
boyd d. & Hargittai E. (2010) 'Facebook privacy settings: Who cares?' First Monday 15, 8 (July 2010), at http://firstmonday.org/htbin/cgiwrap/bin/ojs/index.php/fm/article/view/3086/2589
Cabello F., Franco M.G. & Haché A. (2013) 'The Social Web beyond 'Walled Gardens': Interoperability, Federation and the Case of Lorea/n-1' PsychNology Journal 11, 1 (2013) 43 - 65, at http://www.psychnology.org/File/PNJ11(1)/PSYCHNOLOGY_JOURNAL_11_1_CABELLO.pdf
CFP (2010) 'A Social Network Users' Bill of Rights' Computers, Freedom & Privacy Conference, June 2010, at http://www.cfp2010.org/wiki/index.php/A_Social_Network_Users%27_Bill_of_Rights
Clarke R. (1994) 'Information Infrastructure for The Networked Nation' Xamax Consultancy Pty Ltd, November 1994, at http://www.rogerclarke.com/II/NetNation.html, Extract from Section 2.4 at http://www.rogerclarke.com/II/NetN2.html
Clarke R. (1999) 'Person-Location and Person-Tracking: Technologies, Risks and Policy Implications' Proc. 21st International Conf. Privacy and Personal Data Protection, Hong Kong, September 1999. Revised version published in Info. Techno. & People 14, 1 (2001) 206-231, at http://www.rogerclarke.com/DV/PLT.html
Clarke R. (2002) 'e-Consent: A Critical Element of Trust in e-Business' Proc. 15th Bled Electronic Commerce Conference, Bled, Slovenia, 17-19 June 2002, at http://www.rogerclarke.com/EC/eConsent.html
Clarke R. (2004a) 'Very Black 'Little Black Books'' Xamax Consultancy Pty Ltd, February 2004, at http://www.rogerclarke.com/DV/ContactPITs.html
Clarke R. (2004b) 'Open Source Software and Open Content as Models for eBusiness' Proc. 17th International eCommerce Conference, Bled, Slovenia, 21-23 June 2004, PrePrint at http://www.rogerclarke.com/EC/Bled04.html
Clarke R. (2006) 'What's 'Privacy?' Submission to the Australian Law Reform Commission, Xamax Consultancy Pty Ltd, July 2006, at http://www.rogerclarke.com/DV/Privacy.html
Clarke R. (2007) 'Business Models to Support Content Commons' SCRIPT-ed Special Issue on 'Creating Commons' 4,1 (2007) 59-71 at http://www.law.ed.ac.uk/ahrc/script-ed/vol4-1/clarke.asp, PrePrint at http://www.rogerclarke.com/EC/BMSCC.html
Clarke R. (2008a) 'B2C Distrust Factors in the Prosumer Era' Proc. CollECTeR Iberoamerica, Madrid, 25-28 June 2008, pp. 1-12, Invited Keynote Paper, at http://www.rogerclarke.com/EC/Collecter08.html
Clarke R. (2008b) 'Web 2.0 as Syndication' Journal of Theoretical and Applied Electronic Commerce Research 3,2 (August 2008) 30-43, at http://www.jtaer.com/portada.php?agno=2008&numero=2#, Preprint at http://www.rogerclarke.com/EC/Web2C.html
Clarke R. (2010a) 'An Evaluation of the Terms of Service and Privacy Policy of the LinkedIn Professional Networking Service' Xamax Consultancy Pty Ltd, December 2010, at http://www.rogerclarke.com/EC/LinkedIn-1012.html
Clarke R. (2010b) 'Internet Users' Second-Party Exposure' , at Xamax Consultancy Pty Ltd, December 2010, http://www.rogerclarke.com/EC/IU-SPE-1012.html
Clarke R. (2011) 'The Cloudy Future of Consumer Computing' Proc. 24th Bled eConference, June 2011, at http://www.rogerclarke.com/EC/CCC.html
Clarke R. (2013) 'Consumer-Oriented Social Media: The Identification of Key Characteristics' Working Paper, Xamax Consultancy Pty Ltd, February 2013, at http://www.rogerclarke.com/II/COSM-1301.html
Clarke R. (2014) 'Privacy and Social Media: An Analytical Framework' Forthcoming, Journal of Law, Information and Science 24 (March 2014), PrePrint at http://www.rogerclarke.com/DV/SMTD13.html
Clarke R. & Wigan M.R. (2011) 'You Are Where You've Been The Privacy Implications of Location and Tracking Technologies' Journal of Location Based Services 5, 3-4 (December 2011) 138-155, at http://www.rogerclarke.com/DV/YAWYB-CWP.html
Cohen J. (2013) 'A critical overview of the privacy debates regarding Facebook and an assessment of the 'Anti-Facebook' social network, Diaspora*' MA Thesis, University of the Witwatersrand, Johannesburg, February 2013, at http://mobile.wiredspace.wits.ac.za/bitstream/handle/10539/13131/Jenifer%20CohenThesis%20F.pdf?sequence=2
Cox J. (2007) 'Tim Berners-Lee Warns of 'Walled Gardens' for Mobile Internet' The New York Times, 15 November 2007, at http://www.nytimes.com/idg/IDG_002570DE00740E1800257394004818F5.html?ex=1352869200&en=d4abf597b593be42&ei=5088&partner=rssnyt&emc=rss
Enders A., Hungenberg H., Denker H.P. & Mauch S. (2008) 'The long tail of social networking: Revenue models of social networking sites' European Management Journal (2008) 26, 199- 211, at http://www.esat.kuleuven.be/pub/nj_bscw.cgi/d54738/END08.pdf
Esguerra R. (2011) 'An Introduction to the Federated Social Network' Electronic Frontier Foundation, 21 March 2011, at https://www.eff.org/deeplinks/2011/03/introduction-distributed-social-network
Franchi E. & Tomaiuolo M. (2012) 'Software Agents for Distributed Social Networking' in De Paoli F. & Vizzari G. (eds.), Proc. 13th Workshop on Objects and Agents (WOA 2012), Milano, Italy, September 17-19, 2012, at http://ceur-ws.org/Vol-892/paper4.pdf
Gallagher R. (2013) 'Software that tracks people on social media created by defence firm' The Guardian, 10 February 2013, at http://www.guardian.co.uk/world/2013/feb/10/software-tracks-social-media-defence
GFW (2011) 'Who is harmed by a "Real Names" policy?' Geek Feminism Wiki, at http://geekfeminism.wikia.com/wiki/Who_is_harmed_by_a_%22Real_Names%22_policy%3F, accessed 3 August 2011
Handel M. (2011) 'Privacy in Social Networks' in Asaj N. et al. (eds), Proc. Third Seminar on Research Trends in Media Informatics, Institute of Media Informatics, Ulm University, 7-8 February 2011, pp. 77-82, at http://d-nb.info/1016626320/34#page=77
Harris W. (2006) 'Why Web 2.0 will end your privacy' bit-tech.net, 3 June 2006, at http://www.bit-tech.net/columns/2006/06/03/web_2_privacy/
Helft M. (2010) 'Critics Say Google Invades Privacy With New Service' The New York Times, 12 February 2010, at http://www.nytimes.com/2010/02/13/technology/internet/13google.html?_r=1
Howe J. (2006) 'The Rise of Crowdsourcing' Wired 14.06 (June 2006), at crowds.htmlhttp://www.wired.com/wired/archive/14.06/crowds.html
Kaplan A.M. & Haenlein M. (2010) 'Users of the world, unite! The challenges and opportunities of social media' Business Horizons 53, 1 (Jan-Feb 2010) 59-68, slide-set at http://www.slideshare.net/studente1000/kaplan-andreas-m-haenlein-michael-2010-users-of-the-world-unite-the-challenges-and-opportunities-of-social-media-business-horizons-vol-53-issue-1-p-5968
Krotoski A. (2012) 'Online identity: is authenticity or anonymity more important?' The Guardian, at April 2012, at http://www.guardian.co.uk/technology/2012/apr/19/online-identity-authenticity-anonymity/print
Lankton N. & McKnight D. H. (2011) 'What Does it Mean to Trust Facebook? Examining Technology and Interpersonal Trust Beliefs' The Data Base for Advances in Information Systems 42, 2 (2012) 32-54
McKeon M. (2010) 'The Evolution of Privacy on Facebook' Self-Published, May 2010, at http://mattmckeon.com/facebook-privacy/
Mann S. (2002) 'Cyborglogs ("glogs")' Wearcam.org, 2002, at http://wearcam.org/glogs.htm
Matlin C. (2010) 'With Google Buzz, your closest circle of friends is wide open' The Washington Post, 28 February 2010, at http://www.washingtonpost.com/wp-dyn/content/article/2010/02/26/AR2010022606639.html
Michael K. & Clarke R. (2013) 'Location and Tracking of Mobile Devices: Überveillance Stalks the Streets' Forthcoming, Computer Law & Security Review 29, 2 (March-April 2013), PrePrint at http://www.rogerclarke.com/DV/LTMD.html
Moglen E. (2010) 'Freedom In the Cloud: Software Freedom, Privacy, and Security for Web 2.0 and Cloud Computing' Software Freedom Law Center, 5 February 2010, at http://www.softwarefreedom.org/events/2010/isoc-ny/FreedomInTheCloud-transcript.html
Musiani F. (2010) 'When social links are network links: The dawn of peer-to-peer social networks and its implications for privacy' Observatorio (OBS*) Journal, vol.4 - no3 (2010), 185-207, at http://halshs.archives-ouvertes.fr/docs/00/57/93/42/PDF/Musiani_2010_P2PPrivacy.pdf
Narayanan A., Barocas S., Toubiana V, Nissenbaum H. & Boneh D. (2012) 'A Critical Look at Decentralized Personal Data Architectures' arXiv: 1202.4503, 22 February 2012, at http://arxiv.org/abs/1202.4503
NYT (2010) 'Facebook Privacy: A Bewildering Tangle of Options' The New York Times, 12 May 2010, at http://www.nytimes.com/interactive/2010/05/12/business/facebook-privacy.html
O'Connor R. (2012) 'Facebook is Not Your Friend' Huffington Post, 15 April 2012, at http://www.huffingtonpost.com/rory-oconnor/facebook-privacy_b_1426807.html
Opsahl K. (2010) 'Facebook's Eroding Privacy Policy: A Timeline' Electronic Frontier Foundation, 28 April 2010, at https://www.eff.org/deeplinks/2010/04/facebook-timeline/
O'Reilly T. (2005) 'What Is Web 2.0? Design Patterns and Business Models for the Next Generation of Software' O'Reilly, 30 September 2005, at http://www.oreillynet.com/lpt/a/6228
Osterwalder A. & Pigneur Y. (2002) 'An e-Business Model Ontology for Modeling e-Business' Proc. 15th Bled Electronic Commerce Conf., June 17 - 19, 2002, at http://www.hec.unil.ch/yp/pub/02-bled.pdf
Rappa M. (2003) 'Business Models on the Web', 2003, at http://digitalenterprise.org/models/models.html
Rheingold H. (1993) 'The virtual community: homesteading on the electronic frontier' HarperPerrenial, New York, 1993
Shane D, (2010) 'Facebook is "deliberately killing privacy", says Schneier' Information Age, 13 October 2010, at http://www.information-age.com/technology/security/1290603/facebook-is-%22deliberately-killing-privacy%22-says-schneier
Smarr J. et al. (2007) 'A Bill of Rights for Users of the Social Web' OpenSocialWeb, September 2007, orig, at http://www.opensocialweb.org/, copy at http://www.template.org/?page_id=599/2007/09/05/bill-of-rights/
Smith G. (2004) 'Folksonomy: social classification' Mendeley, 3 August 2004, at http://www.mendeley.com/research/folksonomy-social-classification/
Svantesson D. & Clarke R. (2010) 'Privacy and Consumer Risks in Cloud Computing' Computer Law & Security Review 26, 4 (July 2010) 391-397
van Dijck J. & Nieborg D. (2009) 'Wikinomics and its discontents: a critical analysis of Web 2.0 business manifestos' New Media & Society 11, 4 (2009) 855-874, at http://www.gamespace.nl/content/Wikinomics_and_its_discontents_2009.pdf
Waugh R. (2012) 'Unfair and unwise': Google brings in new privacy policy for two billion users - despite EU concerns it may be illegal' Daily Mail, 2 March 2012, at http://www.dailymail.co.uk/sciencetech/article-2108564/Google-privacy-policy-changes-Global-outcry-policy-ignored.html
Wilde W.D. & Swatman P.A. (1999) 'A Preliminary Theory of Telecommunications Enhanced Communities' Proc. 12th Int'l Bled Electronic Commerce Conf., Bled, Slovenia, June 7 - 9, 1999
Wilson C., Steinbauer T., Wang G., Sala A., Zheng H. & Zhao B.Y. (2011) 'Privacy, Availability and Economics in the Polaris Mobile Social Network' Proc. ACM Workshop on Mobile Computing Systems and Applications (HotMobile 2011), at http://www.cs.ucsb.edu/~ravenben/publications/pdf/polaris-hotmobile11.pdf
Womack B. (2013) 'Facebook Seen Reporting Faster Sales Growth on Ad Demand' Bloomberg News, 31 January 2013, at http://www.bloomberg.com/news/2013-01-30/facebook-seen-reporting-faster-sales-growth-on-mobile-ad-demand.html
Yeung C.M.A., Liccardi I., Lu K., Seneviratne O. & Berners-Lee T. (2009) 'Decentralization: The Future of Online Social Networking, in: W3C Workshop on the Future of Social Networking, 2009, at http://www.w3.org/2008/09/msnws/papers/decentralization.pdf
This paper has been in gestation for a decade, since the release of the early social networking service, Plaxo (Clarke 2004a). The primary stimuli for its development were invitations from Neils Christian Juul of Roskilde University in June 2012 to present a seminar on privacy, trust and user-involvement, and from Andrew Adams at Meiji University in Tokyo to present a keynote at the Asian Privacy Scholars' Network Conference in Tokyo in November 2012. This resulted in the related paper, Clarke (2013).
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in the Cyberspace Law & Policy Centre at the University of N.S.W., and a Visiting Professor in the Research School of Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 13 April 2012 - Last Amended: 31 December 2014 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/II/COSM-1402.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy