Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
This page contains the Appendices to a paper submission to Datenschutz und Datensicherheit (DuD) at http://www.rogerclarke.com/DV/Biel15-DuD.html
Draft of 16 August 2015
© Xamax Consultancy Pty Ltd, 2015
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/DV/Biel15-DuDA.html
Extract from AHRC (2015), emphases added
Summary of Clarke (1997, 2006)
Privacy is not a simple concept, but rather a construct of considerable complexity. The variety can be usefully explained by means of what I refer to as 'dimensions' and which some other authors prefer to call 'aspects' or 'types' (Finn et al. 2013). For discussions of these dimensions, see Clarke (1997-, 2006, 2014b).
The deepest-seated need is for privacy of the physical person. A person who is in danger, wet and cold, or seriously hungry, does not have the luxury of worrying about needs higher up the Maslowian hierarchy. On the other hand, people in many societies enjoy pleasant living conditions, and place considerable value on four further dimensions of their privacy, for psychological, social, economic and political reasons.
Individuals have an interest in being able to communicate with people who they choose to interact with, without others being privy to the conversation. Speech has always been at risk of being overheard, and since at least the early days of the telegraph in the 1840s, messages have been subjected to electronic interception. Moreover, unlike earlier forms of surveillance, electronic interception is usually conducted covertly. The Snowden revelations have caused far more people to appreciate that invasions of the privacy of human communications have reached epidemic proportions and that law enforcement agencies see interception capacity as an entitlement.
There was limited need to assert rights to data privacy while personal data was scattered across discrete physical records and read only by the few people who could gain access to each of them. Since the application of computing technologies to administrative data commencing about 1955, however, the privacy of personal data has also been subject to a rapidly-rising crescendo of intrusive behaviours and applications of technologies (Clarke 1988).
During the 1970s, business and government moved to defuse public concerns by creating a chimera rather than a shield. The express purpose of the OECD Guidelines was "to advance the free flow of information between Member countries and to avoid the creation of unjustified obstacles to the development of economic and social relations among Member countries" (OECD 1980). As a result, the real function of 'data protection' laws is not to protect personal data, let alone the person, but to authorise privacy-invasive behaviours by organisations subject to a limited regulatory framework.
People have an interest in having considerable freedom to behave as they wish, subject only to the constraints of avoiding harm to the interests of others, of communities and societies. An individual's behaviour may be constrained by means of acts directly against their person, or by indirect influences, in particular through surveillance.
Surveillance constrains how people act, whether it is conducted in a physical manner (using the eyes and ears of humans), aided by technologies (such as directional microphones and recording apparatus), or entirely automatically. For discussions, see Clarke (2000, 2001a, 2007, 2009b, 2010). Covert surveillance causes many people to have a generalised fear of the 'pan-optic', and this can have an even more substantial impact on their freedom of behaviour. The pan-optic 'chilling effect' ranges from being highly desirable (where it creates a disincentive for criminal, sociopathic or psychopathic behaviour) to highly undesirable (where it reduces artistic creativity, scientific and engineering inventiveness, economic innovation or political speech).
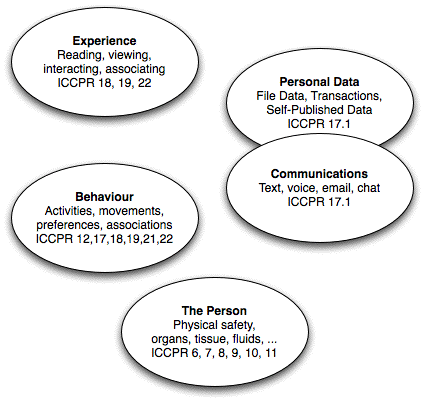
A further dimension of human concerns has been threatened by technological changes of the first two decades of the new century. What an individual reads and views, and the ideas that they gain access to through meetings and other events, have been converted from unrecorded ephemera to stored data. This is achieved through the logging of content sought (search-terms), text read (e-books and web-pages), audio listened to, and image and video viewed. That data is under the control of, and exploitable by, for-profit corporations, and is available to government agencies. The privacy of personal thought may not yet be directly under assault, but the privacy of personal experience is a dangerously close proxy for it.
All of the dimensions of privacy outlined in Appendix 3 are readily recognisable in the UDHR (1948) and ICCPR (1966).
This dimension of privacy is subject to formally-recognised freedoms including the right to life (ICCPR Article 6), right to freedom from torture and non-consensual experimentation (7), freedom from slavery (8), liberty and security and freedom from arbitrary arrest and detention (9), the right to humane treatment (10), and equality before the law (14).
Formally-recognised freedoms relevant to this dimension of privacy include freedom from arbitrary or unlawful interference with correspondence (ICCPR 17), freedom of conscience and religion (18), freedom of expression and the right to seek, receive and impart information and ideas (19), and the rights to peaceful assembly (21) and freedom of association (22).
The ICCPR, although not AGREED until 1966, was based on the 1948 UDHR document. UDHR predates administrative applications of computing, and as a result the concept of personal data does not appear in either document. The primary civil right that supports data privacy is generally regarded as being freedom from arbitrary or unlawful interference with privacy (Article 17).
Formally-recognised freedoms relevant to this dimension of privacy include the rights to liberty and security of person and against arbitrary arrest or detention (ICCPR 9), freedom of movement (12), freedom from arbitrary or unlawful interference with privacy, family and home (17), freedom of conscience and religion (18), the right to hold opinions, freedom of expression, and freedom to seek, receive and impart information and ideas (19), the rights to peaceful assembly (21) and freedom of association (22), and the right to participation in public affairs, to vote and to be elected (25).
Formally-recognised freedoms relevant to this dimension of privacy include freedom of movement (12), freedom from arbitrary or unlawful interference with privacy and correspondence (17), freedom of thought, conscience and religion (18), the freedom to seek and receive information and ideas (19), the right to peaceful assembly (21), freedom of association (22), and the right to participation in public affairs (25).
Means are needed for people to interact with other individuals, broadcast messages, and collaborate with others, without being subject to the highly exploitative business model of contemporary social networking services, and without exposing their profiles, identities and locations. Categories of 'persons-at-risk' who have particular need for such a service include victims of domestic violence, protected witnesses and undercover operatives (Clarke 2001c, GFW 2011). Table 5 identifies key features of COSM.
Extract from Clarke (2014a)
AHRC (2015) 'Rights and freedoms: right by right' Australian Human Rights Commission, Aprtil 2015, at http://www.humanrights.gov.au/rights-and-freedoms-right-right-0
Clarke R. (1988) 'Information Technology and Dataveillance' Commun. ACM 31,5 (May 1988) Re-published in C. Dunlop and R. Kling (Eds.), 'Controversies in Computing', Academic Press, 1991, PrePrint at http://www.rogerclarke.com/DV/CACM88.html
Clarke R. (1994) 'Human Identification in Information Systems: Management Challenges and Public Policy Issues' Information Technology & People 7,4 (December 1994) 6-37, PrePrint at http://www.rogerclarke.com/DV/HumanID.html
Clarke R. (1997) 'Introduction to Dataveillance and Information Privacy, and Definitions of Terms' Xamax Consultancy Pty Ltd, August 1997, revisions to March 2015, at http://www.rogerclarke.com/DV/Intro.html
Clarke R. (2000) 'Technologies of Mass Observation' Notes for the 'Mass Observation Movement' Forum, Melbourne, 26 October 2000, at http://www.anu.edu.au/people/Roger.Clarke/DV/MassObsT.html
Clarke R. (2001a) 'While You Were Sleeping ... Surveillance Technologies Arrived' Australian Quarterly 73, 1 (January-February 2001), PrePrint at http://www.rogerclarke.com/DV/AQ2001.html
Clarke R. (2001b) 'Person-Location and Person-Tracking: Technologies, Risks and Policy Implications' Information Technology & People 14, 2 (Summer 2001) 206-231, PrePrint at http://www.rogerclarke.com/DV/PLT.html
Clarke R. (2001c) 'Research Challenges in Emergent e-Health Technologies' Xamax Consultancy Pty Ltd, July 2001, at http://www.rogerclarke.com/EC/eHlthRes.html#PAR
Clarke R. (2006) 'What's 'Privacy'?' Xamax Consultancy Pty Ltd, August 2006, at http://www.rogerclarke.com/DV/Privacy.html
Clarke R. (2007) 'The Regulation of Surveillance' Xamax Consultancy Pty Ltd, August 2007, at http://www.rogerclarke.com/DV/SReg.html
Clarke R. (2009a) The Covert Implementation of Mass Vehicle Surveillance in Australia' Proc. 4th Workshop on the Social Implications of National Security: Covert Policing, April 2009, ANU, Canberra, at http://www.rogerclarke.com/DV/ANPR-Surv.html
Clarke R. (2009b) 'A Framework for Surveillance Analysis' Xamax Consultancy Pty Ltd, August 2009, at http://www.rogerclarke.com/DV/FSA.html
Clarke R. (2010) 'What is Überveillance? (And What Should Be Done About It?)' IEEE Technology and Society 29, 2 (Summer 2010) 17-25, at http://www.rogerclarke.com/DV/RNSA07.html
Clarke R. (2013) 'Consumer-Oriented Social Media: The Identification of Key Characteristics' Xamax Consultancy Pty Ltd, February 2013, at http://www.rogerclarke.com/II/COSM-1301.html
Clarke R. (2014a) 'The Prospects for Consumer-Oriented Social Media' Proc. Bled eConference, June 2014, PrePrint at http://www.rogerclarke.com/II/COSM-1402.html
Clarke R. (2014b) 'Privacy and Free Speech' Invited Presentation at the Australian Human Rights Commission Symposium on Free Speech, Sydney, 7 August 2014, Xamax Consultancy Pty Ltd, August 2014, at http://www.rogerclarke.com/DV/PFS-1408.html
Finn R.L., Wright D. & Friedewald M. (2013) 'Seven Types of Privacy' pp. 3032 of Gutwirth S., Leenes R., de Hert P. & Poullet Y. (eds.) 'European Data Protection: Coming of Age' Springer, 2013
GFW (2011) 'Who is harmed by a "Real Names" policy?' Geek Feminism Wiki, undated, apparently of 2011, at http://geekfeminism.wikia.com/wiki/Who_is_harmed_by_a_%22Real_Names%22_policy%3F
ICCPR (1996) 'International Covenant on Civil and Political Rights' United Nations, 1966, at http://www.ohchr.org/en/professionalinterest/pages/ccpr.aspx
OECD (1980) 'OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data' OECD, 1980, at http://www.oecd.org/internet/ieconomy/oecdguidelinesontheprotectionofprivacyandtransborderflowsofpersonaldata.htm
UDHR (1948) 'Universal Declaration of Human Rights' United Nations, 10 December 1948, at http://www.un.org/en/documents/udhr/index.shtml
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in the Computer Science at the Australian National University.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 12 March 2015 - Last Amended: 16 August 2015 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/DV/Biel15-DuDA.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy