Roger Clarke's Web-Site
© Xamax Consultancy Pty Ltd, 1995-2024

Infrastructure
& Privacy
Matilda
Roger Clarke's Web-Site© Xamax Consultancy Pty Ltd, 1995-2024 |

|
|||||
| HOME | eBusiness |
Information Infrastructure |
Dataveillance & Privacy |
Identity Matters | Other Topics | |
| What's New |
Waltzing Matilda | Advanced Site-Search | ||||
Working Version of 23 August 2017
© Xamax Consultancy Pty Ltd, 2017
Available under an AEShareNet ![]() licence or a Creative
Commons
licence or a Creative
Commons  licence.
licence.
This document is at http://www.rogerclarke.com/ID/BiomRegI.html
The term 'RegTech' emerged in 2016 as a means of adding sex-appeal to the application of technology to the compliance responsibilities of corporations in the financial services sector. A broader vision is that RegTech is needed in all industry sectors, and by regulatory agencies as well as by organisations that are subject to regulatory requirements.
Might biometric applications have an important role to play in RegTech? A review of the nature of biometric technologies and the array of real-world challenges that confront their application, combined with a thought-experiment based on registration of company directors, suggests maybe not.
The term 'RegTech' was coined recently within the financial services sector to refer to "the use of new technologies to solve regulatory and compliance requirements more effectively and efficiently" (IIF 2016, p.2. See also Arner et al. 2016). Potential applications exist far beyond that sector, however, and can assist not only organisations that are subject to regulatory requirements, but also regulatory agencies, and the organisations and individuals that are the intended beneficiaries of the process (Clarke 2017).
Identity is presumed to play a key role in most regulatory schemes. The suggestion has accordingly arisen that biometrics could be an important element within the RegTech arena. The purpose of this paper is to consider that proposition. It does so on the basis of a thought-experiment based on a particular regulatory measure that has been considered in many countries.
The paper commences by reviewing the nature of biometrics and the challenges that confront real-world implementations of biometric technologies. It would be highly desirable to evaluate the potential role of biometrics by means of deep case studies of real-world circumstances. Unfortunately, there is a great shortage of them, because of the habitual secrecy with which the biometrics industry has always worked. Even where open technology and process standards exist, analysis is hampered because critical elements are proprietary and closed. Independent evaluations are rarely published. Assertions without supporting evidence are made by provider and user organisations alike. Engagement with affected individuals, their representatives, and public interest advocacy organisations are almost entirely unknown. For example, the 30-year records of the Australian Privacy Foundation include no evidence of any consultation processes being undertaken in relation to any of the many implementations of biometrics in the country. Given the serious shortage of suitable case studies, a thought-experiment is conducted, in an area in which behaviour that gives rise to serious financial harm in well-known to occur.
What appears to be the earliest formal reference on RegTech envisages biometrics to be part of the technology mix: "When coupled with biometrics technology to enable fingerprint and iris scanning, face recognition, but also remote passport recognition and eIDs, advanced analytics can allow for more efficient ways to verify an individual's identity to access financial services" (IIF 2016). Further, one of the first academic papers to emerge on the topic wrote approvingly of the 'India Stack' for RegTech, whose foundation is "a national system of biometric identification" (Arner et al. 2016). (India has imposed an authoritarian biometrics regime called Aadhar, in defiance of claims before the courts of breach of the constitutional right to privacy - Greenleaf 2016).
In the RegTech arena, as in so many others, some key questions need to be confronted:
Biometric technologies have a history of failure and industry turnover. The entry-halls in Australian airports are currently in tumult because of the failures of the once-much-vaunted facial 'recognition' system. Even with false-acceptance ratios turned up high, they don't work as claimed. It doesn't help matters that the design of passenger flows within the terminal appears to be remarkably incompetent. Fingerprints represent a less inadequate basis for biometric schemes, but they too have proven in many circumstances to be incapable of being effectively applied. The latest great hope of the industry appears to be iris recognition. In the absence of published, independent testing, impact assessments and public consultations, we have to await the tales of embarrassments, failures, unjustified suspicion, compromise and cover-up that will doubtless emerge in this arena as well.
Biometric technologies are confronted by a fundamental problem: the list of strongly desirable attributes of a biometric is quite long, and the contenders don't satisfy them (Shen & Tan 1999). Further, a wide range of technical features of biometrics create challenges for designers (Mansfield & Wayman 2002). These include:
Technical inadequacies are exacerbated by further aspects of the socio-technical systems into which biometric technologies are injected:
For a rich selection of problems and sources, see Schneier (1999), Jain et al. (2004), Schneier 2009, Babbage (2010) and Magnet (2011). A succinct summary is: 'biometrics are all about convenience, not security'. [Declaration: I stole that epigram from security consultant Steve Wilson; but Steve was talking specifically about Apple TouchID, and he said "consumer biometrics are all about convenience, not security" (Wilson 2013, my emphasis). The words in my text are an epigram, i.e. a short, pithy statement, not a quotation.]
The Australian Privacy Foundation was and remains astonished at the naiveté of so many of the organisations that have flirted with biometric applications. Its Policy Statement on Biometrics provides a layman's introduction to biometrics, summarises ten problems it perceives, and concludes that "No new biometric schemes should be implemented until and unless comprehensive laws have been brought into effect to regulate them" (APF 2008).
The most common application of biometrics is what is misleadingly referred to as 'verification', but is far more appropriately called 'authentication'. This involves a 1-to-1 comparison between a newly-captured biometric and that or those previously recorded for the particular person who the newly-presenting person is asserted to be. A second application is what is commonly referred to 'identification', involving a 1-to-n search for a match to a newly-captured biometric within a population, in many cases a large population.
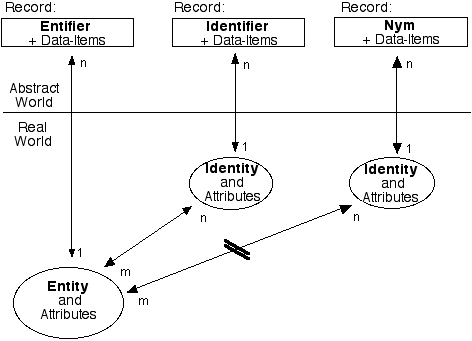
However, designers commonly fail to recognise that biometrics is not about identification or identity authentication, but rather about entification or entity authentication. As depicted by Figure 1, biometrics cut through identities (such as Company Secretary and Clinic Practice Manager) and deal in sensitive personal data relating to the person who is presumed (often incorrectly) to be the user of the identity, and, moreover, to be the sole user of it.
Extract from Clarke (2010)
The assessment of biometric technologies and their applications in this section is almost entirely negative. The reasons for this are the necessity of brevity, and the need to counterbalance the excessive claims made by proponents. There are contexts in biometric technologies can be a useful and adequately reliable element within a design; but there are far fewer contexts than the technologies' proponents would like their customers to believe; and the complexity of the design features needed to accommodate biometrics' vast array of deficiencies is often so great as to nullify those contributions. The following section takes into account both these problems and the technologies' threatening nature, and considers whether biometrics might nonetheless have contributions to make to RegTech.
In order to gain some insight into the application of biometrics in the field of RegTech, this section presents a thought-experiment. A particular concern that gets news coverage every few years is the phenomenon sometimes referred to as 'phoenix companies'. This particular white-collar scam involves a company going into liquidation owing a considerable amount of money, but with the assets and the going concern transferred to another company without the liabilities travelling with them.
So what's the problem that biometrics could address? A recurrent proposition, adopted in a few countries and again under consideration in others, is that company directors should be required to register, and to quote their registration-code (a 'Director Identification Number') when they perform particular actions. See generally Anderson et al. (2017).
The safeguards that are being sought are that:
The creation of a registration-id for directors, whether name-and-date-of-birth or a number, in itself achieves none of these things. But perhaps the proposal could be restructured to use an entifier instead of, or as well as, an identifier. However, there would need to be many elements of such a scheme. In particular:
Such a scheme would in itself do nothing to locate individuals sought for prosecution - unless of course the collection of biometric measures has by then become normalised, and every, say, border-crossing, traffic infringement, random alcohol and drug test, civil ceremony, etc. involves biometric collection and comparisons against multiple wanted-persons lists. It's not clear that even the most repressive governments have achieved such arrangements yet, but biometrics providers live in hope. Where suspects were located, the results of comparisons of a new biometric measure against that recorded in the register would be likely to be compelling evidence in a trial.
An indication of the scale of such an activity can be gained by examining a medium-sized jurisdiction. Australia is roughly comparable with The Netherlands and Texas. There are about 2.5m Australian corporations (ASIC 2017), and of these 11,500 are in the frame (Anderson et al. 2017), suggesting that needles represent c. 0.5% of the haystack. Corporations are, like cyberspace, merely 'shared hallucinations', so it is impossible to apply biometrics to them (and remarkably challenging even to design effective identification and identity authentication processes). The focus therefore falls on the c. 2,500 of perhaps 250,000-500,000 distinct director identities, or 0.5-1.0% of that particular haystack. (No count or estimate of the number of company directors has been located on ASIC's site, in Anderson's work or elsewhere).
In short, the proposition is to impose a biometric scheme - of a kind achieved in very few of even the most aggressively authoritarian nation-states - on several hundred thousand individuals, in the hope of constraining the activities of a cumulative total of perhaps 2,000 individuals over the last few years who have committed offences, in particular under s.592 of the Corporations Act.
Given the breast-beating indulged in by politicians when the issue gains media prominence, it would reasonably be expected that phoenix company activities are serious criminal offences. On the other hand, in Australia at least, this is far from clear. On the one hand "Illegal phoenix activity is a serious crime and may result in company officers (directors and secretaries) being imprisoned" (ASIC 2013), but on the other hand no indication of the nature of the offence is provided in that reference, in Anderson (2017) or in media reports, other than vague mentions of 'the directors' duties provisions'. Media searches failed to find any reports of cases. The Phoenix Task Force led by the Australian Tax Office (ATO) offers only two unidentified case studies, one of which is claimed to have achieved a prosecution for fraud (implying that it was under the Crimes Act rather than the Corporations Act), and the other of which was said to have resulted in increased assessments and penalties but with no mention of a prosecution, successful or otherwise (ATO 2017). This matters, because the absence of evidence of prosecutions undermines the credibility of a proposition that draconian biometric measures are necessary and proportionate.
In summary, all directors, throughout the country, would present themselves, initially and every time thereafter when they want to perform a regulated action, to the regulatory agency (whose footprint is currently almost entirely limited to capital-city offices, so perhaps instead to a suitable and suitably-managed third party organisation that has footprints throughout the country), be subjected to biometric procedures, and perhaps have one or more biometrics stored in a database that is subject to multiple further uses.
At some stage during the development, implementation or operation of the scheme, the challenges and failure modes discussed in the previous section would become publicly visible, and the scope for error and failure would be obvious to all. Directors of small companies have a degree of clout, and the big end of town has a great deal of it. It is difficult to see any government surviving the attempt to implement such a scheme, nor any incoming government failing to close the project down. All of this is completely foreseeable. Application of the well-known but frequently-ignored standards of transparency, justification and proportionality might just save the careers of some budding statespeople.
The phoenix company analysis in the previous section was a thought-experiment, not a case study. Its selection was random, not careful. It might be 'a straw man', and its choice might reflect author bias. The impracticability and negative payback that are apparent from the analysis may or may not be a common feature of biometric applications in RegTech. The arguments advanced in this paper need to be subjected to critique and complemented by deep cases studies of real-world projects.
Subject to those qualifications, a couple of key messages emerge from experience with a range of biometrics projects combined with the above thought-experiment:
Before starting to think about biometrics as a possible solution, it's crucial to know what the problem is that you're trying to solve.
All biometric schemes face substantial technical challenges, and require pre-planned arrangements for multiple exception-conditions that will arise frequently. This is particularly so in contexts that involve large volumes of transactions, or that are subject to multiple failure-modes, especially where some players are motivated to subvert or attack the scheme.
At some stage, the real nature of the scheme, and its shortfalls, will both become abundantly apparent. A great many people will dislike it intensely. Many of them will be powerful enough to cause the scheme's sponsors a great deal of grief.
As in other areas of biometric technologies, user organisations that consider biometrics as a form of RegTech need to avoid getting caught up in supplier hype, and evaluate the possibilities calmly and realistically. Cartels of user-and-provider organisations such as the Biometrics Institute need to be broken down, not just for the public's benefit, but also for that of the shareholders in companies that get sucked into spending money on ineffective technologies. (Despite the home-page claim of being "a user group with a majority of user members", as at July 2017, user organisations represented only 42% of the Biometric Institute's membership, and supplier members 50%).
From a public policy perspective, propositions for the design and application of privacy-invasive technologies need to be subject to a set of meta-principles (APF2013) - every one of which is conventional and accepted, yet far too often applied. It's possible that biometrics may have a role to play somewhere in the RegTech arena; but the path is strewn with risks for developers, regulatees and regulators, and great care is strongly advisable.
Anderson H., Ramsay I., Welsh M. & Hedges J. (2017) 'Phoenix Activity: Recommendations on Detection, Disruption And Enforcement' Melbourne Law School and Monash Business School, February 2017, at http://law.unimelb.edu.au/__data/assets/pdf_file/0020/2274131/Phoenix-Activity-Recommendations-on-Detection-Disruption-and-Enforcement.pdf
Arner D.W., Barberis J. & Buckley R.P. (2016) 'FinTech, RegTech and the Reconceptualization of Financial Regulation' Northwestern Journal of International Law and Business, PrePrint of October 2016 at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2847806
APF (2008) 'Biometrics' Policy Statement, Australian Privacy Foundation, April 2008, at http://www.privacy.org.au/Papers/Biometrics.html
APF (2013) 'Meta-Principles for Privacy Protection' Australian Privacy Foundation, March 2013, at http://www.privacy.org.au/Papers/PS-MetaP.html
ASIC (2013) 'Small business-illegal phoenix activity' Australian Securities and Investment Commission, November 2013, at http://asic.gov.au/for-business/your-business/small-business/compliance-for-small-business/small-business-illegal-phoenix-activity/
ASIC (2017) '2017 Company registration statistics' Australian Securities and Investment Commission, at http://asic.gov.au/regulatory-resources/find-a-document/statistics/company-registration-statistics/2017-company-registration-statistics/, copy extracted 31 July 2017
ATO (2017) 'Phoenix Taskforce' Australian Tax Office, July 2017, at https://www.ato.gov.au/General/The-fight-against-tax-crime/Our-focus/Illegal-phoenix-activity/Phoenix-Taskforce/?=redirected#Newsandresults
Babbage (2010) 'Biometrics: The Difference Engine: Dubious security' The Economist, October 2010, at http://www.economist.com/blogs/babbage/2010/10/biometrics
Clarke R. (2010) 'A Sufficiently Rich Model of (Id)entity, Authentication and Authorisation' Proc. IDIS 2009 - The 2nd Multidisciplinary Workshop on Identity in the Information Society, LSE, London, 5 June 2009, PrePrint at http://www.rogerclarke.com/ID/IdModel-1002.html
Clarke R. (2017) 'A Framework for RegTech' Working Paper, Xamax Consultancy Pty Ltd, August 2017, at http://www.rogerclarke.com/EC/RTF.html
Greenleaf G.W. (2016) 'Your Money or Your Life?: Modi's Deceptive Enactment of India's ID Legislation' Privacy Laws & Business International Report 140 (April 2016) 18-20, at https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2800835
IIF (2016) 'RegTech in Financial Services: Technology Solutions for Compliance and Reporting' Institite of International Finance', March 2016, at https://perma.cc/VKM6-HP8L
Jain A.K., Pankanti S., Prabhakar S., Hong L., Ross A. & Wayman J.L. (2004) 'Biometrics: A Grand Challenge' Proc. Int'l Conf. on Pattern Recognition, Cambridge, UK, Aug. 2004, at http://www.cedar.buffalo.edu/~govind/CSE666/fall2007/Biometrics_GC.pdf
Magnet S.A. (2011) 'When Biometrics Fail: Gender, Race and the Technology of Identity' Duke Uni. Presss, 2011
Mansfield A.J. & Wayman J.L. (2002) 'Best Practices in Testing and Reporting Performance of Biometric Devices' U.K. National Physical Laboratory, August 2002, at http://face-rec.org/databases/mansfield02.pdf
Schneier B. (1999) 'Biometrics: Uses and Abuses' Commun. ACM 42,8 (August 1999) 135-136, at https://www.schneier.com/essays/archives/1999/08/biometrics_uses_and.html
Schneier B. (2009) 'Tigers use scent, birds use calls - biometrics are just animal instinct' The Guardian, 8 January 2009, at https://www.theguardian.com/technology/2009/jan/08/identity-fraud-security-biometrics-schneier-id
Shen W. & Tan T. (1999) 'Why Use Biometrics-Based Personal Identification?' Proc. National Academy of Sciences (PNAS) 96, 20 (September 1999) 11065-11066, at http://www.pnas.org/content/96/20/11065.full.pdf
Wilson S. (2013) 'How Bart Simpson might defend TouchID' Lockstep, 23 Sep 2013, at http://lockstep.com.au/blog/2013/09/23/bart-simpson-and-touchid
An early version of this paper was presented at the 10th Workshop on the Social Implications of National Security (SINS17), Sydney, 9 August 2017. Thanks to Katina Michael and Rob Nicholls for proposing that this topic was in need of investigation.
Roger Clarke is Principal of Xamax Consultancy Pty Ltd, Canberra. His quarter-century of consultancy work in the eBusiness arena includes many assignments on identity and biometrics matters. He is also a Visiting Professor in Cyberspace Law & Policy at the University of N.S.W., and a Visiting Professor in Computer Science at the Australian National University. He has been a Board member of the Australian Privacy Foundation since its establishment in 1987, and was its Chair 2006-14.
| Personalia |
Photographs Presentations Videos |
Access Statistics |
 |
The content and infrastructure for these community service pages are provided by Roger Clarke through his consultancy company, Xamax. From the site's beginnings in August 1994 until February 2009, the infrastructure was provided by the Australian National University. During that time, the site accumulated close to 30 million hits. It passed 65 million in early 2021. Sponsored by the Gallery, Bunhybee Grasslands, the extended Clarke Family, Knights of the Spatchcock and their drummer |
Xamax Consultancy Pty Ltd ACN: 002 360 456 78 Sidaway St, Chapman ACT 2611 AUSTRALIA Tel: +61 2 6288 6916 |
Created: 31 July 2017 - Last Amended: 23 August 2017 by Roger Clarke - Site Last Verified: 15 February 2009
This document is at www.rogerclarke.com/ID/BiomRegI.html
Mail to Webmaster - © Xamax Consultancy Pty Ltd, 1995-2022 - Privacy Policy